Everything You Need to Know About Phishing Attacks
Published April 5, 2025.

Phishing attacks are on the rise and ensnaring ever more victims. In fact, 76% of businesses have reported being a victim of a phishing attack in the last year and the number of such instances has grown by 65% in that year.
The statistics for phishing attacks are so significant that protecting yourself against them is one of the best ways to secure yourself in cyberspace. Phishing attacks account for an entire 90% of all data breaches, a fact that doesn’t diminish the seriousness of other threats, but does make it crucial that you know how to spot and react against a phishing attack.
The price of falling victim to a phishing attack is also high, averaging $3.86m. Knowing these facts, how do you go about defending yourself against this threat? The first step is understanding how a phishing attack works.
What Does a Phishing Attack Look Like?
But what’s in it for the attackers? After all, most people are at least somewhat intuitive and mindful – it takes a fair amount of work to fool someone into interacting with a harmful email. Attackers can collect valuable data on individuals or entire organizations, enjoy access to systems and networks for future assaults like ransomware attacks, or directly harm computer infrastructure if that is their goal. In any case, the organization bears the cost.
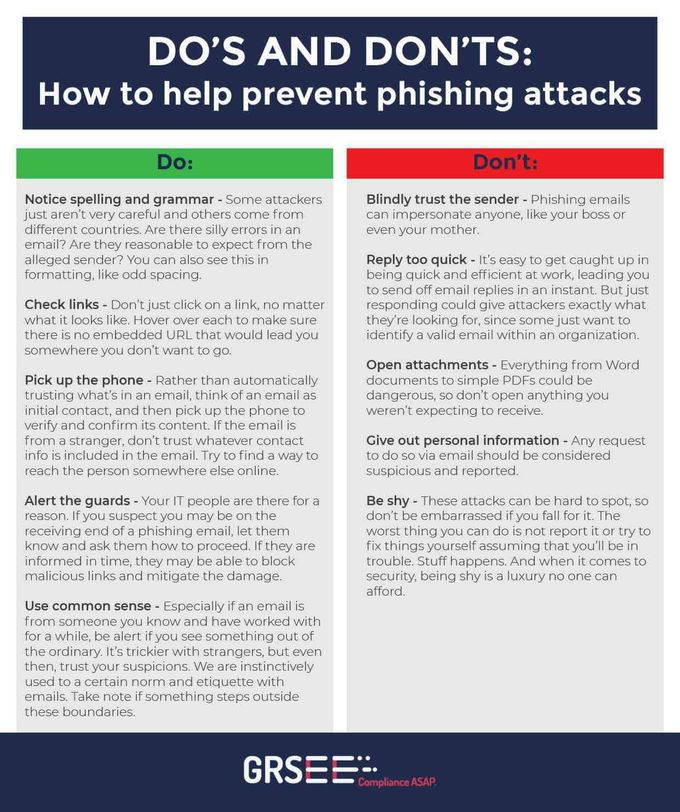
Do’s and Don’ts to Help Prevent Phishing Attacks
Understanding the process an attacker goes through in targeting your organization can help you understand best how to combat them. Luckily, there are some steps you can take and certain habits you can get into that will drastically decrease the likelihood of falling victim to this kind of attack.
A lot of work goes into making phishing attacks successful and it can be quite difficult to spot a sophisticated, well-informed attack. A really precise attacker could even send you emails that seem to be from family members and co-workers. If you want to save your organization time, money and heartbreak, it’s always best to establish protocols that have you constantly, automatically and intuitively on guard.