How to Integrate OWASP ZAP With Other Security Tools
Explore practical ways to integrate OWASP ZAP with existing systems, ensuring comprehensive security and efficient vulnerability management.
Published April 5, 2025.

Web application vulnerabilities are a constant concern for businesses, exposing them to potential breaches and data theft. In fact, according to Verizon, they are implicated in approximately 25% of all data breaches. OWASP ZAP (Zed Attack Proxy), formally known now as ZAP, stands out as a widely trusted, open-source tool for detecting and addressing these security weaknesses. With its features and affordability, it has become a favorite among developers and security teams for maintaining secure applications.
» Looking for a fast solution? Contact us to receive comprehensive security coverage
OWASP ZAP: A Brief Overview
OWASP Zed Attack Proxy, now rebranded simply as ZAP, is a popular open-source tool created by the Open Web Application Security Project (OWASP) to identify vulnerabilities in web applications. Acting as a proxy-based scanner, ZAP analyzes traffic between clients and servers to detect and mitigate security weaknesses.
Its user-friendly interface and features like automated scanning and advanced scripting make it accessible to both developers and security teams.
ZAP’s flexibility shines through its seamless integration into CI/CD pipelines, enabling continuous security testing in dynamic development environments. Its support for plugins and extensions allows users to customize the tool to fit their specific needs, making ZAP a trusted choice for enhancing web application security across industries.
» Want to ensure secure development? Read our guide to SDL for Agile workflows
OWASP ZAP vs. Other Vulnerability Scanners
OWASP ZAP is a leading tool in web application security, offering unique advantages over other scanners like Burp Suite and Acunetix. Its open-source nature, affordability, and strong community support make it particularly appealing to organizations seeking reliable and flexible security solutions.
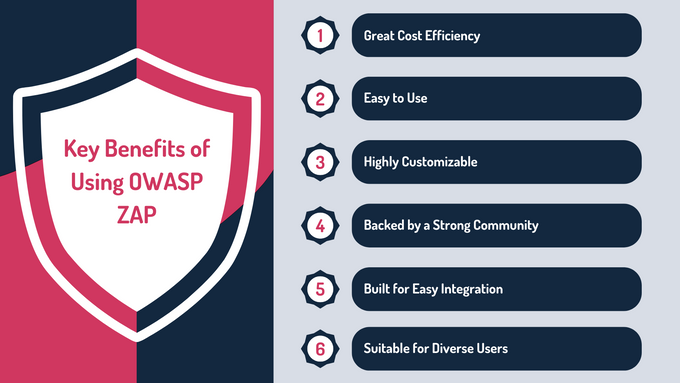
Benefits of OWASP ZAP
- Cost efficiency: Being free and open-source, OWAP ZAP minimizes costs for organizations without sacrificing functionality.
- Ease of use: ZAP offers an intuitive interface designed to accommodate both beginners and seasoned professionals, simplifying the process of identifying and addressing vulnerabilities.
- Customizability: Offers extensive modification options through plugins and scripts, allowing users to adapt the tool to their unique needs.
- Community support: Backed by an active community that continuously provides updates, resources, and improvements.
- Integration capabilities: Seamlessly integrates with CI/CD pipelines, automating security processes effectively. Other tools often require premium versions for similar features.
- Broad appeal: ZAP is suited for a diverse audience, including developers and security teams, catering to various organizational needs.
» Not sure about vulnerability scans? Discover how vulnerability scans compare to penetration testing
In this regard, OWASP ZAP stands out as an accessible and flexible security tool, offering robust features and strong community support. Its open-source design allows organizations to integrate security seamlessly into workflows, making it a versatile choice for teams of all sizes.
Using ZAP With Other Security Solutions
OWASP ZAP is a powerful tool on its own, but when combined with other security solutions, it transforms into a comprehensive defense mechanism. Integrating ZAP together with tools like Burp Suite, Nessus, and Nmap can help organizations create a multi-layered security strategy that addresses vulnerabilities at every level.
1. Combining ZAP With Vulnerability Scanners
OWASP ZAP complements vulnerability assessment tools like Nessus and Nmap, creating a more robust security workflow. These integrations enable the sharing of data, automated scans, and enhanced coverage of vulnerabilities across applications and networks.
Benefits of Integrating Zap With Vulnerability Scanners
Enhanced visibility
Combines application and network-level insights for a holistic view of vulnerabilities.
Improved workflow
Automates repetitive tasks, reducing manual effort and increasing efficiency.
Integration Methods
- API interaction: Utilize ZAP's REST API to automate scans and facilitate data exchange with tools like Nessus.
- Scripting: Create custom scripts in ZAP to pull data from tools such as Nmap or push findings back for a consolidated view.
- Command line tools: Run ZAP in a command-line environment alongside tools like Nmap, combining their capabilities for more extensive testing.
» Maximize your business' cybersecurity with the CIA triad
2. Integrating ZAP Into CI/CD Pipelines
By embedding ZAP into CI/CD pipelines, organizations can ensure security testing is automated and continuous, catching vulnerabilities before they reach production. Let's see how to use OWASP ZAP inside CI/CD pipelines.
Benefits of Integrating Zap Into CI/CD Pipelines
Early detection
Catches vulnerabilities during development stages, reducing the cost of remediation.
Continuous feedback
Provides developers with real-time insights to improve code security.
Reduced risk
Ensures secure builds, lowering the likelihood of vulnerabilities in production environments.
» Discover all there is to know about risk assessments and the risk assessment process
Integration Methods
- ZAP Docker Image: Use ZAP’s Docker image to run scans automatically during builds.
- Scripted scans: Incorporate ZAP’s command-line options into deployment scripts for seamless execution.
- Reporting: Configure ZAP to generate reports that flag critical issues, gating insecure deployments.
3. Strengthening Security Monitoring With ZAP-SIEM Integration
Integrating OWASP ZAP with SIEM platforms like Splunk or ELK Stack strengthens an organization’s ability to detect and respond to security incidents effectively. This collaboration brings together application security and broader security monitoring efforts.
Benefits of ZAP-SIEM Integration
Holistic view
Combines application vulnerabilities with network and endpoint security data for a comprehensive security perspective.
Improved incident response
Correlating ZAP findings with broader security metrics accelerates threat detection and mitigation efforts.
ZAP-SIEM Integration Tips
- Log forwarding: Forward ZAP logs to the SIEM for centralized monitoring and analysis. This ensures that vulnerabilities identified by ZAP are part of the organization’s overall threat detection framework.
- Alerts and dashboards: Leverage SIEM tools to generate automated alerts based on ZAP findings. Create custom dashboards to visualize vulnerabilities and correlate them with other security incidents.
» Ready to enhance security monitoring? Discover how SOC 2 helps achieve a stronger security posture
Plugins to Maximize ZAP Functionality
Similar to the security tools we've discussed, OWASP ZAP greatly benefits from plugins. These extensions improve its scanning accuracy, enhance reporting capabilities, and enable seamless integration with other security tools.
Open-Source Plugins for Enhanced Scanning
Open-source plugins are an excellent way to boost ZAP's core functionality, adding features tailored to specific needs:
- Passive scanner rules: Enhance passive scanning with additional rules for identifying specific vulnerabilities.
- JSON and XML reporting: Generate custom report formats for seamless integration with external reporting tools.
- OWASP dependency-check: Identify vulnerabilities in project dependencies by scanning for known issues.
- WebSocket support: Extend ZAP’s scanning abilities to include WebSocket communications for improved coverage.
- Enhanced active scan rules: Add community-contributed rules to actively check for vulnerabilities like SQL Injection or Cross-Site Scripting (XSS).
These plugins are community-driven and freely available, making them accessible to organizations of all sizes.
» Protect yourself from common vulnerabilities: Learn how penetration testing helps
Commercial Plugins for Advanced Use Cases
For organizations seeking more advanced features, commercial plugins provide enhanced capabilities:
- ZAP in action: Offers guided scans and advanced reporting features, ideal for teams requiring detailed insights and easy usability.
- Burp Suite integration: Enables interoperability between ZAP and Burp Suite, combining their strengths for comprehensive testing.
- Fortify and Veracode integrations: Sync ZAP findings with these commercial static analysis tools for a holistic security assessment.
Common Limitations of ZAP and How to Address Them
1. Business Logic Vulnerabilities
ZAP may struggle to detect issues that arise from an application’s workflow, such as improper authorization or unconventional user interactions. These vulnerabilities require contextual understanding, which is best addressed through manual testing or tools specializing in business logic assessments.
2. Complex Authentication Flaws
Multi-factor authentication and intricate session management often pose challenges for ZAP. These scenarios demand advanced testing capabilities or manual validation, which can be supported by tools like Burp Suite for better coverage.
3. Security Misconfigurations
ZAP focuses primarily on web vulnerabilities, often overlooking infrastructure-level misconfigurations. Tools like Nessus or manual infrastructure reviews are better suited for identifying and addressing these issues.
| Problem | Why ZAP Struggles | How to Address It |
|---|---|---|
| Business Logic Vulnerabilities | Requires contextual understanding of application workflows, beyond automated checks. | Use manual testing or tools specializing in business logic vulnerabilities. |
| Complex Authentication Flaws | Multi-factor authentication and session management are often too complex for ZAP. | Supplement with tools like Burp Suite or manual validation processes. |
| Security Misconfigurations | Focused on web vulnerabilities, and missing infrastructure-level issues. | Leverage infrastructure scanning tools like Nessus or conduct manual reviews. |
When Integration Becomes Necessary
There are specific scenarios where ZAP requires integration with other tools:
- Comprehensive coverage: To identify vulnerabilities outside ZAP’s detection scope, such as infrastructure flaws or business logic issues.
- Automated workflows: For seamless integration into CI/CD pipelines, enabling automated security checks during deployment.
- Advanced analysis: When deeper threat intelligence or advanced vulnerability management features from tools like Nessus or Burp Suite are required.
Important Note: Leveraging ZAP with advanced tools strengthens its utility, ensuring seamless workflows and tackling vulnerabilities beyond its scope. Integrating tools like Nessus for scanning or manual testing for business logic flaws provides comprehensive coverage across all layers.
Leverage ZAP Today
Integrating OWASP ZAP with other security tools offers a powerful and comprehensive approach to vulnerability management. By leveraging ZAP's strengths in dynamic application security testing (DAST) alongside the capabilities of other tools, you can create a more holistic security posture. Whether it's combining ZAP with static analysis tools for shift-left security, vulnerability scanners for broader coverage, or reporting platforms for streamlined analysis, the possibilities are vast.
» Ready to strengthen your organization's security? Contact us to learn more