How to Secure Your External Network With Regular Penetration Testing
With external networks constantly exposed to cyber threats, organizations need a proactive security approach. In this article, we'll explore the importance of regular penetration testing, detailing key benefits, testing methodologies, and how businesses can strengthen their defenses against attacks.
Updated April 7, 2025.

As organizations expand their digital operations, the need for strong cybersecurity measures has never been greater. Cybercriminals continuously seek opportunities to exploit weaknesses in systems, targeting businesses of all sizes. Public-facing assets such as web servers, VPNs, and cloud services are particularly vulnerable as they are the first point of contact between an organization and the internet. A staggering 54% of organizations identify third parties and external networks as their most susceptible areas, emphasizing the need for proactive security strategies.
One of the most effective ways to secure these critical assets is through regular penetration testing. Unlike traditional security measures, penetration testing simulates real-world attacks, helping organizations identify and remediate vulnerabilities before they can be exploited.
» Is your organization secure against cyber threats? Find out with a pentest
Understanding External Network Penetration Testing
Penetration testing, often referred to as pentesting, is a simulated cyberattack used to identify vulnerabilities in an organization’s systems before malicious actors can exploit them.
Mimicking real-world attack scenarios provides critical insights into weaknesses in networks, applications, and security protocols. In this regard, one of the most crucial areas to test is an organization’s external network—the systems and assets exposed to the public internet.
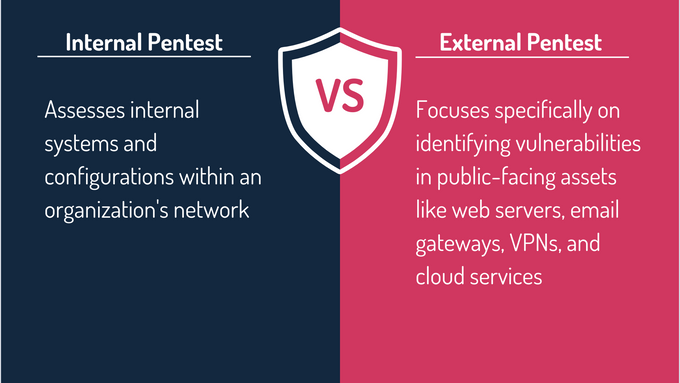
Internal vs External Penetration Testing
External network penetration testing focuses specifically on identifying vulnerabilities in public-facing assets like web servers, email gateways, VPNs, and cloud services. Unlike internal penetration testing, which assesses systems within an organization's firewall, external testing simulates attacks from an outsider's perspective, targeting areas most accessible to cybercriminals.
While application-focused testing dives into the security of specific software or web applications, external testing ensures the broader infrastructure supporting these applications is secure against unauthorized access.
» Struggling to understand the different types? Learn more in our guides to the types of penetration testing and gray box pentesting
Key Benefits of Regular External Penetration Testing
- Proactive risk mitigation: Detecting vulnerabilities before they can be exploited allows organizations to stay ahead of emerging threats. Regular external pentesting provides insight into security weaknesses, enabling businesses to remediate issues before they lead to a breach.
- Improved network segmentation: Ensuring proper segmentation between public-facing systems and internal networks is crucial for reducing the spread of attacks. External penetration testing helps identify misconfigurations or weak points where unauthorized access could lead to lateral movement.
- Enhanced visibility of overlooked assets: Organizations often have exposed systems, forgotten services, or outdated applications that go unnoticed. Regular external pentesting helps identify these overlooked assets, ensuring they are properly secured or decommissioned.
- Regulatory compliance (HIPAA, PCI DSS, ISO 27001): Many industries are required to conduct regular security assessments to meet compliance standards. External penetration testing helps organizations satisfy compliance requirements for HIPAA or PCI DSS by demonstrating proactive security measures. Compliance with frameworks like ISO 27001 not only prevents fines but also reassures stakeholders that sensitive data is well protected.
- Business continuity through minimized disruptions: A successful cyberattack on external-facing systems can lead to downtime, data loss, and financial harm. Regular penetration testing helps prevent these disruptions by identifying vulnerabilities before they become entry points for attackers. Strengthening external defenses ensures ongoing operations remain secure and uninterrupted.
» Here's how to overcome the challenges of PCI DSS penetration testing
How Attackers Exploit External Networks
External networks are the first line of defense between an organization and potential attackers, making them a prime target for exploitation. Cybercriminals continuously scan these networks for vulnerabilities that can provide unauthorized access, disrupt operations, or steal sensitive data.
Common Attack Methods
- Scanning for open ports: Attackers use tools to identify open ports, which can serve as entry points into a network if left unprotected or improperly configured.
- Exploiting unpatched systems: Outdated software and systems with known vulnerabilities are easy targets for attackers looking to gain access or escalate privileges.
- Man-in-the-middle (MITM) attacks: By intercepting data transmissions between systems, attackers can eavesdrop, alter, or steal sensitive information without detection.
The Risks of Misconfigurations and Weak Network Defenses
Even the most sophisticated security tools are ineffective if network configurations are flawed. Misconfigured firewalls, exposed services, and weak authentication protocols can create openings for attackers to exploit.
These vulnerabilities often go unnoticed until it's too late, highlighting the importance of regular penetration testing to identify and correct security gaps before they can be used against the organization.
The Penetration Testing Process for External Networks
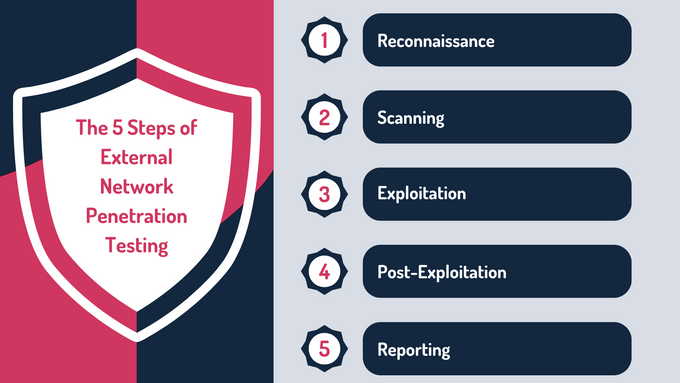
External network penetration testing follows a structured process designed to uncover vulnerabilities in public-facing systems. This method simulates real-world attacks to identify weaknesses that could be exploited by malicious actors, ensuring organizations can address security gaps proactively.
1. Reconnaissance
The first phase involves gathering as much information as possible about the target network. Testers collect data on IP addresses, domain names, and external services to understand the organization’s attack surface. Passive and active reconnaissance techniques help identify potential vulnerabilities without alerting the target.
Best practices include:
- Clearly defining the assets, objectives, and boundaries of the assessment
- Identifying which external systems (e.g., web servers, VPNs, cloud services) will be tested and specify any exclusions to avoid service disruptions
- Providing accurate documentation and understanding the goals—whether it’s maintaining good compliance, vulnerability identification, or resilience testing
» Did you know? The cloud might not be safe anymore
2. Scanning
Once the reconnaissance phase is complete, testers use scanning tools to map the network and detect open ports, active devices, and running services. Tools like Nmap and Nessus help identify vulnerabilities related to unpatched systems, misconfigured services, or outdated protocols. Scanning provides a detailed picture of the network’s structure, highlighting potential entry points for attackers.
» Confused? Read our guide to vulnerability scanning vs. penetration testing
3. Exploitation
In this phase, testers attempt to exploit the vulnerabilities identified during scanning to gain unauthorized access. Techniques may include leveraging weak passwords or insecure configurations. The goal is to simulate how a real attacker would breach the network, providing insight into how far an intrusion could go if left unchecked.
4. Post-Exploitation
After gaining access, testers evaluate the potential impact of a successful attack. This includes determining what sensitive data could be accessed, how an attacker might maintain persistence, and the potential for lateral movement within the network. Post-exploitation helps organizations understand the full scope of risk associated with identified vulnerabilities.
» Understand what's involved in the risk assessment process
5. Reporting
The final phase involves compiling a comprehensive report detailing the findings from the test. This includes a list of discovered vulnerabilities, the methods used to exploit them, and the potential risks to the organization. The report also provides actionable recommendations for remediation, helping you strengthen your organization's external defenses.
» Learn more: Penetration testing steps from pre-engagement to reporting
Common Vulnerabilities Found in External Network Penetration Tests
- Open ports: Exposed ports can provide entry points for attackers if left unprotected or improperly restricted.
- Unpatched firmware: Outdated firmware on network devices often contains known vulnerabilities that hackers can exploit.
- Misconfigured firewalls: Weak firewall rules may allow unnecessary traffic or fail to block unauthorized access attempts.
- Weak segmentation: Poorly segmented networks can allow attackers to move laterally once inside, escalating their access.
- Default credentials: Devices and applications with factory-set usernames and passwords are easy targets for brute-force attacks.
Uncovering these vulnerabilities highlights gaps in an organization's security posture, often revealing issues with patch management, configuration oversight, and access controls. Regular external pentesting ensures that these weaknesses are identified and remediated before they can be leveraged by attackers.
» Exposed ports and weak firewalls invite attackers. Identify security gaps before attackers do
Essential Tools and Methodologies for External Penetration Testing
External penetration testing relies on a combination of specialized tools and industry-recognized frameworks to identify and assess vulnerabilities effectively. These tools help testers scan networks, exploit weaknesses, and analyze security gaps, while frameworks provide structured methodologies to ensure comprehensive assessments.
Tools for External Network Testing
- Nmap: A powerful network scanning tool used to discover open ports, active services, and potential vulnerabilities.
- Metasploit: A widely used exploitation framework that helps simulate real-world attacks on identified vulnerabilities.
- Nessus: A vulnerability scanner that detects misconfigurations, outdated software, and security flaws in network systems.
- OpenVAS: An open-source vulnerability assessment tool that provides in-depth network security scanning and reporting.
- Wireshark: A network protocol analyzer that helps testers inspect traffic patterns and detect suspicious activity.
Best Frameworks for External Penetration Testing
- PTES (Penetration Testing Execution Standard): Defines a structured approach for conducting penetration tests, from reconnaissance to reporting.
- OSSTMM (Open Source Security Testing Methodology Manual): A methodology focused on security assessments and risk analysis for network environments.
- CIS Benchmarks: A set of security best practices for securing various systems, applications, and network configurations.
Summary: External penetration testing uses tools like Nmap and Metasploit to find vulnerabilities, while frameworks like PTES and OSSTMM ensure structured assessments for stronger security.
Limitations of External Network Penetration Testing
While external penetration testing is an essential security measure, it does have limitations that organizations should consider. These challenges can impact the effectiveness of testing and should be supplemented with additional security strategies to ensure continuous protection.
Limitations of External Network Penetration Testing
- Coverage gaps: External testing focuses on internet-facing assets and may not detect internal threats or vulnerabilities within the network.
- Resource intensity: Conducting a thorough penetration test requires skilled professionals, specialized tools, and significant time investment.
- False positives: Automated scanners may flag vulnerabilities that are not exploitable, leading to wasted time on unnecessary fixes.
- Point-in-time limitations: Pentests provide a snapshot of security at a given moment but do not account for new threats that emerge after testing.
Complementary Strategies to Strengthen Security
- Continuous monitoring: Implementing security monitoring tools ensures real-time detection and response to new threats.
- Patch management: Regular updates to software, firewalls, and network devices help eliminate known vulnerabilities before attackers can exploit them.
- Red teaming: Simulated, full-scope attacks test not only technical security but also an organization’s detection and response capabilities.
» Strengthen your organization's security with the CIA triad
Secure Your External Networks With GRSee's Penetration Testing
At GRSee, we believe that securing external networks requires expert-driven assessments, tailored methodologies, and proactive defense strategies. Our team conducts in-depth penetration testing to uncover vulnerabilities in public-facing systems, ensuring your organization stays protected. Through a combination of manual testing and advanced tools, we identify security gaps that automated scans often miss.
What sets our cybserservices apart is our holistic testing process and actionable remediation insights. Each assessment is customized to align with industry standards, regulatory requirements, and business objectives. With clear guidance and expert support, we help organizations fortify their external networks, achieve compliance, and stay ahead of evolving cyber threats.
» Ready to secure your systems? Chat to our experts