How to Secure Your Internal Network With Regular Penetration Testing
Insider threats and misconfigurations are among the biggest risks organizations face today. In this article, we'll explore how regular internal penetration testing uncovers vulnerabilities, prevents privilege escalation, and strengthens security. Learn the best practices, essential tools, and how GRSee can help.
Published April 5, 2025.

Cyber threats within an organization are often overlooked despite their potential for severe damage. Weak access controls, misconfigured systems, and insider threats create pathways for unauthorized access and data breaches. According to Verizon's 2024 Data Breach Investigation Report, insider threats now account for 35% of breaches. This sharp increase highlights the need for organizations to shift their focus beyond external threats and strengthen internal defenses before a security incident occurs.
Strengthening security requires regular internal penetration testing to uncover weaknesses that perimeter defenses miss. Testing privilege escalation, lateral movement, and misconfigurations helps organizations fortify their internal network before an attack occurs.
» Don’t wait for a breach—strengthen internal security with GRSee
What Is Internal Network Penetration Testing?
Internal penetration testing simulates real-world attack scenarios where an attacker has already gained access to an organization's internal systems. This could be due to compromised credentials, insider threats, or malware infections.
The goal is to uncover weaknesses in access controls, network segmentation, and privileged accounts before they can be exploited by real attackers.
» Learn about the different types of penetration tests and their applications
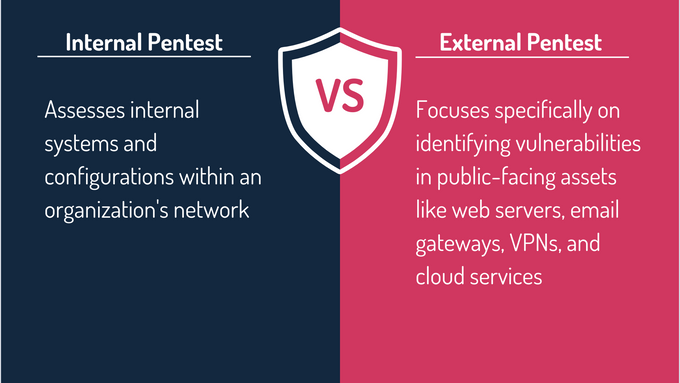
Internal vs. External Penetration Testing: What’s the Difference?
External penetration testing helps organizations secure their internet-facing systems, preventing breaches through firewalls, VPNs, and cloud services. Internal penetration testing takes a different approach by simulating an attacker who is already inside, evaluating their ability to bypass internal controls, escalate privileges, and access sensitive data.
» Curious about pentesting's role in compliance? See how to leverage penetration testing and training in PCI DSS 4.0.1
How Are Internal Networks Compromised?
Weak internal security can make it easy for attackers to escalate access and move deeper into an organization’s systems. Exploiting misconfigurations, stolen credentials, and poor access controls allows them to bypass defenses and reach critical data. Here are the most common ways attackers compromise internal networks:
- Stolen credentials: Phishing, brute force attacks, and credential stuffing provide attackers with unauthorized access to internal systems.
- Misconfigured access controls: Weak active directory settings and excessive privileges create pathways for attackers to escalate access.
- Lateral movement techniques: Once inside, attackers move between systems, exploiting weak segmentation to access sensitive assets.
- Malware & ransomware deployments: Compromised endpoints can be used to deploy malware, encrypt data, or establish persistence for ongoing attacks.
» Looking for a comprehensive approach? Learn about gray box penetration testing
The Internal Penetration Testing Process Step-by-Step
1. Reconnaissance
Internal penetration testing begins with reconnaissance, where testers map the internal network, identify key systems, and gather intelligence on potential attack paths.
This phase involves scanning for open ports, exposed services, and misconfigured active directory settings that could be exploited. The goal is to understand the network structure and pinpoint vulnerabilities before attempting further attacks.
» Make sure you understand the difference between vulnerability scans and penetration tests
2. Exploitation
After reconnaissance, testers attempt to exploit identified weaknesses to gain unauthorized access. This step focuses on privilege escalation, credential misuse, and exploiting unpatched vulnerabilities.
Tools like Metasploit may be used to extract login credentials or exploit misconfigurations. Successfully gaining higher privileges allows the attacker to access critical systems and move deeper into the network.
3. Lateral Movement
Once inside, attackers seek to expand access across the network. Lateral movement techniques involve leveraging compromised accounts, misconfigured permissions, and weak segmentation to navigate between systems.
Using tools like BloodHound, testers assess how an attacker could escalate privileges and reach sensitive data, domain controllers, or high-value assets.
4. Post-Exploitation
After gaining access to multiple systems, the next step is assessing how much damage an attacker could inflict. Testers evaluate data exposure risks, potential persistence mechanisms, and the organization’s ability to detect unauthorized activity.
This phase simulates how a real attacker might exfiltrate sensitive data, deploy malware, or disrupt operations once inside the network.
» Here are the ways malware can bypass endpoint protection
5. Reporting & Remediation
The final phase of internal penetration testing involves documenting findings, assessing risk levels, and providing actionable remediation steps. Organizations receive a detailed report outlining exploited vulnerabilities, attack pathways, and recommendations for strengthening security. Fixing weak access controls, improving network segmentation, and enforcing least privilege policies are key remediation actions to prevent real-world attacks.
» Learn more: Penetration testing steps from pre-engagement to reporting
Benefits of Regular Internal Penetration Testing
- Early detection of insider threats: Malicious insiders and compromised accounts threaten internal security. Regular testing uncovers unauthorized access before it leads to a breach.
- Stronger network segmentation & access control: Poor segmentation lets attackers move freely. Testing identifies weak access controls to keep sensitive assets protected.
- Reduced risk of privilege escalation attacks: Attackers exploit misconfigured permissions to gain higher access. Internal testing highlights excessive privileges and weak authentication.
- Compliance with PCI DSS, HIPAA, ISO 27001, GDPR: Security regulations require regular assessments. Internal testing ensures security controls function as needed for compliance.
- Improved incident response & threat detection: Understanding attack methods helps teams refine their response. Simulated attacks enhance detection and mitigation strategies.
How Often Should Internal Penetration Testing Be Conducted?
Regular internal penetration testing is essential for identifying security gaps before they can be exploited.
The ideal testing frequency depends on factors like industry regulations, data sensitivity, and organizational risk level. While annual testing provides a strong baseline, quarterly assessments are recommended for high-risk industries such as finance, healthcare, and government.
Key Events for Security Testing
Certain events necessitate immediate testing to ensure security controls remain effective. Major IT changes, security incidents, and compliance audits introduce new risks that need evaluation. Conducting penetration tests after these key events helps organizations stay protected.
- After major IT changes: System upgrades, cloud migrations, and infrastructure expansions can introduce vulnerabilities that require assessment.
- Post-security incident: Any breach or insider threat should prompt immediate testing to identify weaknesses and prevent further compromise.
- As part of a compliance audit: Regulatory frameworks like PCI DSS, HIPAA, and ISO 27001 require regular security testing to validate internal controls.
» The cloud might not be safe anymore: See how AWS penetration testing strengthens security
Common Internal Security Vulnerabilities Found in Penetration Tests
Internal penetration tests often uncover security gaps that can be exploited by attackers or malicious insiders that can go unnoticed for long periods, increasing the risk of data breaches, lateral movement, and insider threats. Addressing these weaknesses is essential for maintaining a secure internal network:
- Weak passwords & credential mismanagement: Poor password policies, reused credentials, and lack of multi-factor authentication make it easy for attackers to gain access.
- Misconfigured active directory & unnecessary privileges: Weak active directory settings and excessive user permissions allow attackers to escalate privileges and move laterally.
- Unpatched systems & outdated software: Missing security updates leave systems vulnerable to known exploits, increasing the risk of unauthorized access.
- Lack of network segmentation allowing lateral movement: Flat networks enable attackers to spread across internal systems without restriction, making containment difficult.
- Exposed file shares & sensitive data leaks: Misconfigured file shares and open databases allow unauthorized users to access confidential data.
Regular internal penetration testing identifies security gaps before they can be exploited. Strengthening access controls and enforcing least privilege reduces risk while ensuring compliance with industry standards.
Best Practices for Scoping an Internal Penetration Test
Properly scoping an internal penetration test ensures accurate, relevant, and actionable results. Without clear objectives, organizations risk overlooking critical vulnerabilities or testing areas that do not align with business needs. The following best practices help define a comprehensive and effective internal security assessment.
1. Define Critical Assets & High-Value Systems
Understanding which assets hold the most sensitive data or business-critical functions is essential. Testing should prioritize systems such as:
- Domain controllers: Key targets for privilege escalation.
- Financial and HR systems: Often contain personally identifiable information (PII).
- R&D and intellectual property servers: Can be prime targets for insider threats.
2. Set Realistic Attack Simulation Goals
Not all penetration tests are the same—some focus on compliance, while others assess real-world attack resilience. Establishing clear testing objectives ensures security teams gather useful and actionable insights. Common goals include:
- Identifying how an attacker could escalate privileges from a compromised user account.
- Assessing the effectiveness of existing security controls against internal threats.
- Testing incident detection and response capabilities.
3. Identify Privilege Escalation Risks
Attackers often start with low-level access and seek to elevate privileges to compromise critical systems. Scoping the test to identify weak authentication controls, excessive permissions, and privilege escalation paths helps mitigate internal security risks before they are exploited.
4. Ensure the Test Aligns With Compliance Requirements
Many organizations conduct penetration tests to meet regulatory standards such as PCI DSS, HIPAA, or ISO 27001. Ensuring the test evaluates security controls relevant to compliance helps organizations satisfy audit requirements and strengthen their overall security posture.
Main takeaway: A well-scoped penetration test provides realistic, actionable findings that help organizations reinforce internal security and prevent misconfigurations, insider threats, and unauthorized access.
5. Implement Key Frameworks for Internal Testing
Industry-recognized methodologies ensure organizations receive comprehensive insights into their security posture, including:
- CIS controls: Provides best practices for securing internal networks, including access control and network segmentation.
- NIST guidelines: Establishes security standards for penetration testing, ensuring organizations follow structured testing methodologies.
» Compare NIST to ISO 27001 here
Addressing the Limitations of Internal Penetration Testing
1. Testing Is Point-in-Time; Threats Evolve Daily
Penetration tests provide a snapshot of an organization's security posture at a specific moment. However, new vulnerabilities, misconfigurations, and attack techniques emerge constantly.
To stay protected, supplement periodic penetration testing with continuous monitoring, real-time threat detection, and regular audits.
2. Automated Tools May Generate False Positives
While automated tools efficiently scan for vulnerabilities, they often flag low-risk issues or misinterpret normal system behavior as threats. Relying solely on automation can lead to wasted resources and overlooked vulnerabilities, while combining expert-driven assessments with automation helps validate findings and prioritize real security risks.
3. Security Teams Must Act on Findings Quickly
Unaddressed vulnerabilities remain open attack vectors even after a penetration test identifies them. Organizations must treat findings as actionable intelligence rather than a compliance checkbox. Clear remediation processes, high-risk prioritization, and rapid IT response are essential to closing security gaps before attackers exploit them.
Secure Your Internal Network With GRSee
GRSee takes a proactive approach to securing your internal network against evolving cyber threats. Our expert-led penetration testing focuses on insider threats, privilege escalation risks, and misconfigurations, helping organizations identify and mitigate security gaps before attackers can exploit them.
Security doesn’t end with testing. Our remediation support and post-test guidance ensure that your team has the insights and strategies needed to strengthen security long-term. Whether addressing compliance requirements or preventing insider-driven breaches, we deliver actionable results that enhance your organization's overall resilience.
» Ready to begin? Contact us today