Mastering Cloud Security: Key Concepts and Best Practices
Discover the key concepts and best practices for secure cloud computing. Learn how to protect your data, prevent breaches, and stay compliant with evolving regulations like GDPR, SOC 2, and HIPAA.
Published March 20, 2025.

Cloud computing has transformed how businesses operate, offering scalability, flexibility, and cost savings. However, this shift has also introduced new security risks: Ransomware attacks, unauthorized access, and data breaches are among the top threats organizations face today
For example, the average cost of a single data breach worldwide has risen by more than 139% from 2014 to 2024, reaching 4.88 million USD per incident. This clearly indicates that businesses must take a proactive approach to secure their assets.
In this article, we explore the key concepts and best practices of cloud security, covering everything from shared responsibility models and security threats to encryption, incident response, and continuous compliance.
» New to cloud security? Contact our experts for a customized and rigorous compliance audit
The Importance of Security in Cloud Computing
Cloud security encompasses the policies, technologies, and practices designed to protect cloud-based systems, data, and infrastructure from cyber threats.
Ensuring security in cloud computing is not solely the responsibility of cloud providers. While providers secure the infrastructure, you're responsible for protecting your data, applications, and access controls. Without a well-defined cloud security threats defense strategy, your organization risks exposure to regulatory penalties, reputational damage, and financial loss.
The shared responsibility model—where cloud providers and users play a role—further emphasizes the need for vigilant, well-defined security strategies to protect assets in transit and at rest.
» Be prepared: Learn about key cybersecurity considerations for international businesses
12 Cloud Security Principles and Best Practices
- Data in transit protection: Use TLS/SSL encryption to secure data as it moves between users and cloud systems—also consider symmetric and asymmetric encryption.
- Asset protection and resilience: Ensure data center security, data backups, and redundancy measures.
- Separation between customers: Prevent one compromised cloud user from affecting another through multi-tenant security controls.
- Operational security: Secure daily cloud operations with vulnerability management, monitoring, and incident response.
- Personnel security: Control employee access to cloud systems and monitor privileged accounts.
- Secure development: Implement DevSecOps to build security into every stage of software development.
- Identity and authentication: Enforce multi-factor authentication (MFA) and identity verification for all cloud users.
- External interface protection: Secure APIs, web interfaces, and command-line tools from unauthorized access.
- Secure service administration: Ensure secure administrative practices such as least privilege access.
- Audit information and alerts: Implement real-time logging and security alerting for compliance and forensic analysis.
- Supply chain security: Ensure third-party vendors comply with security requirements.
- Incident response and recovery: Have a defined response plan for cloud security breaches.
» Learn more: What is compliance and why do you need it?
Shared Responsibility Models Across Cloud Providers
Shared responsibility models clarify which aspects of cloud security your provider manages and which you must handle.
AWS, Azure, and Google Cloud each define these responsibilities differently. Providers secure the underlying infrastructure—physical data centers, networking, and hardware—while you are accountable for securing your data, applications, and configurations.
Understanding these distinctions is critical. If you assume the provider covers all security aspects, you risk leaving vulnerabilities unaddressed, which could expose your organization to breaches and compliance issues.
| Cloud Provider | Provider Responsibilities | Customer Responsibilities |
|---|---|---|
| Google Cloud | Protects physical assets, network infrastructure, and core services, strongly focusing on automated monitoring and risk mitigation. | Responsible for securing data, managing user access, configuring security settings, and ensuring secure application deployment. |
| Azure | Handles physical security, network infrastructure, and the foundational platform services. Emphasizes integrated compliance features. | Oversees data classification, identity management, application security, and proper configuration of cloud resources. |
| AWS | Secures the physical infrastructure, networking, and core services. Provides detailed guidelines for securing the operating system, virtualization, and facilities. | Manages data encryption, identity and access management, application security, and configuration of virtual resources. |
» Learn how AWS penetration testing uncovers hacking risks
Business Implications of Cloud Security
Businesses must actively secure their cloud environment since the cloud is integral to modern operations and data management. You cannot afford to leave security entirely to your provider, as the shared responsibility model demands that you manage your data, applications, and configurations.
Here's a comparison of how secure cloud environments hold up against unsecured ones:
Secure Cloud Environment
- Regular security audits and access controls
- MFA & role-based access control
- Data encryption in transit and at rest
- Defined incident response plan
Unsecured Cloud Environment
- No consistent security monitoring
- Weak authentication policies
- Sensitive data is stored in plaintext
- No clear response strategy for breaches
» Did you know? The cloud might not be safe anymore
Common Security Threats in Cloud Computing
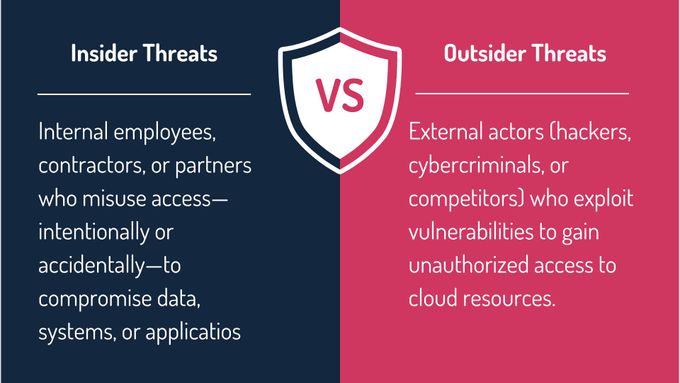
Insider and Outsider Threats
Insider and outsider threats pose significant risks to your cloud environment, and understanding both is critical for effective security management.
For example, an insider might inadvertently share sensitive credentials through poor security practices, while an outsider could use phishing attacks or exploit software vulnerabilities to breach your systems.
To mitigate these risks, you should implement robust access controls, continuous monitoring, and regular security training for employees. Employing multi-factor authentication (MFA) and intrusion detection systems can help you quickly detect and respond to potential breaches.
» See how hackers exploit security vulnerabilities: Learn about the benefits of penetration testing
Account Hijacking and Unauthorized Access
Account hijacking and unauthorized access are serious risks in cloud hosting security. Attackers often use techniques such as phishing, credential stuffing, and exploiting weak or reused passwords to gain unauthorized access.
They may also employ social engineering tactics to trick users into revealing their login credentials and malware or keylogging to capture sensitive information. Such intrusions undermine the security of cloud services and can lead to significant data breaches and operational disruptions.
Key warning signs and preventative measures include:
- Unusual login activity, such as logins from unexpected locations or devices.
- Frequent password reset requests may indicate attempts to compromise accounts.
- Implementation of multi-factor authentication (MFA) to reinforce security.
- Regular monitoring of access logs and alerts for anomalous activities.
- Enforcing strong, unique passwords and periodic password changes.
- Sudden changes in user behavior or access patterns.
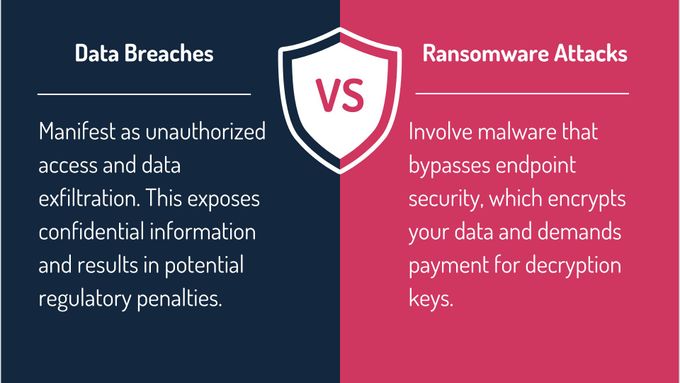
Data Breaches and Ransomware Attacks
Data breaches and ransomware attacks are two critical threats that can compromise your cloud security, yet they manifest in notably different ways.
Data breaches occur when attackers gain unauthorized access to sensitive data, often exploiting vulnerabilities in security protocols or misconfigured systems. In contrast, ransomware attacks involve malicious software that encrypts your data, rendering it inaccessible until a ransom is paid.
Data Breaches:
- Manifest as unauthorized access and data exfiltration.
- Exposes confidential information and incurs potential regulatory penalties.
- Examples include the Capital One breach, which exposed millions of customer records.
Ransomware Attacks:
- Involve malware that bypasses endpoint security, which encrypts your data and demands payment for decryption keys.
- The WannaCry incident is a prime example of organizations worldwide experiencing widespread operational disruption.
» Learn how to handle a ransomware attack
Best Practices for Ensuring Cloud Security
To counter these threats, businesses must adopt industry best practices to secure cloud computing environments. Below are the most effective strategies.
Data Protection and Encryption Strategies
Data protection is a cornerstone of secure cloud computing and adequate cloud-based security. Encrypting your data in transit, at rest, and in use ensures that your information remains confidential and intact, even if unauthorized access occurs.
Encryption in transit protects data as it moves between devices and cloud services. Encryption at rest safeguards stored data from breaches, while encryption ensures that sensitive information remains protected even when actively processed. These practices collectively contribute to robust security in cloud environments.
The table below outlines key protocols and practices:
| Data State | Encryption Protocol/Method | Key Management Practices |
|---|---|---|
| In transit | TLS/SSL | Use secure key exchange mechanisms; implement HSMs. |
| At rest | AES-256, RSA (for key encryption) | Regularly rotate keys; use dedicated key vault services. |
| In use | Memory encryption, Secure enclaves | Monitor access controls; apply runtime protection tools. |
» Choose the best encryption method for your data: Asymmetric vs. symmetric encryption
Identity and Access Management (IAM) and Authentication Controls
Strong identity and access management (IAM) practices are vital for maintaining robust security in cloud environments. You must ensure that only authorized individuals can access critical resources.
Identity and access management (IAM) ensures that only authenticated users access cloud resources.
To achieve this, emphasize the following:
- Multi-factor authentication (MFA) to add extra security.
- Role-based access control (RBAC) to assign role-based permissions.
- The principle of least privilege limits access to sensitive tasks.
These elements work together to reduce the risk of unauthorized access and mitigate potential insider and outsider threats.
These measures will bolster your secure cloud computing framework and help prevent unauthorized access.
Network Security and Infrastructure Hardening
Network security and infrastructure hardening are critical components of secure cloud computing. Protecting your virtual private clouds (VPCs) and implementing robust firewalls and network segmentation can significantly reduce the risk of unauthorized access and lateral movement within your network.
Key best practices include:
- Configuring VPCs to isolate sensitive workloads and using subnets to separate different tiers of your application.
- Deploying firewalls to filter traffic at the network perimeter and within internal networks, thereby blocking unauthorized access.
- Implementing network segmentation to create secure zones that limit exposure.
- Set up dedicated security controls like intrusion prevention systems (IPS) and intrusion detection systems (IDS) to monitor and respond to suspicious activities.
Application Security and DevSecOps Integration
Application security and DevSecOps integration are essential for creating resilient cloud applications that withstand evolving threats. Securing APIs, containers, and the entire software development lifecycle demands a comprehensive approach that embeds security into every development and deployment stage.
DevSecOps: A culture and set of practices that integrate security into every phase of the development process. It emphasizes the collaboration of development, security, and operations teams to automate security measures without compromising agility.
Key practices include:
- Adopting secure coding standards to mitigate common vulnerabilities such as the OWASP Top 10.
- Implementing continuous testing and automated security scans within CI/CD pipelines to detect issues promptly.
- Utilizing threat modeling to anticipate potential attack vectors during the design phase.
- Securing APIs through robust authentication, authorization, and rate limiting.
- Enforcing container security by validating images, limiting privileges, and conducting regular audits of container configurations.
By integrating these measures, you ensure that security is not an afterthought but a continuous, proactive process woven into the fabric of your cloud application development.
Cloud Security Incident Response
An effective cloud security incident response plan is crucial for minimizing damage, restoring operations, and learning from security incidents.
Case Study: The Capital One Data Breach
In the 2019 Capital One data breach, a misconfigured cloud firewall allowed an unauthorized user to access over 100 million customer records. The breach was discovered too late, resulting in $80 million in fines and severe reputational damage.
Incident Response Strategy: Step-By-Step
Here are the key components and practical steps you should incorporate into your incident response strategy:
1. Mission and Goals
- Clearly define the purpose of your incident response plan, such as minimizing damage, protecting sensitive data, and ensuring rapid recovery.
- Establish actionable, measurable goals agreed upon by all stakeholders.
2. Roles and Responsibilities
- Identify the incident response manager, security analysts, and other key personnel (including legal counsel and external vendors).
- Assign specific responsibilities to each team member and ensure everyone knows their role during an incident.
3. Preparation for Cyberthreats
- Conduct regular cybersecurity training and mock drills to ensure readiness.
- Implement and regularly update tools such as intrusion detection systems (IDS), intrusion prevention systems (IPS), and security information and event management (SIEM) solutions.
4. Incident Classification and Prioritization
- Develop a framework for classifying incidents (e.g., critical, high, medium, low) based on severity and impact.
- Prioritize response efforts to focus on threats that pose the most significant risk.
5. Documentation of the Identification Process
- Detail procedures for detecting and confirming incidents, including monitoring tools and escalation protocols.
- Maintain comprehensive logs to support forensic analysis and future audits.
6. Communication Plan
- Establish clear communication protocols for internal teams, management, and external stakeholders.
- Prepare message templates to ensure consistent and accurate information sharing during a breach.
7. Legal and Regulatory Considerations
- Outline steps to meet obligations under data breach laws and industry regulations (e.g., GDPR and HIPAA in healthcare).
- Include legal counsel in the incident response team to manage compliance and mitigate regulatory exposure.
» Learn more about cybersecurity in healthcare
8. Mitigation and Containment Strategies
- Define procedures for isolating affected systems and limiting the spread of the breach.
- Implement strategies such as disconnecting compromised devices or restricting account access to prevent further damage.
9. Third-Party Vendor Management
- Include protocols for engaging with external vendors if their services or data are impacted.
- Document vendor responsibilities, response times, and communication channels.
10. Rapid Recovery Plans
- Detail recovery steps for restoring systems, validating functionality, and ensuring data integrity.
- Develop backup and restoration procedures to expedite recovery following an incident.
11. Post-Incident Review and Evaluation
- Conduct a thorough review to identify what went well, what failed, and how to improve your response strategy.
- Involve all relevant stakeholders in debriefing sessions to update and refine the incident response plan.
Future Trends in Cloud Security
Emerging Threats and Evolving Strategies
Emerging threats and evolving strategies demand that you continually update your approach to cloud technology security. As cyber attackers become more sophisticated, new vulnerabilities emerge, challenging traditional defenses.
To counter these challenges, leverage robust cloud security services in cloud computing that offer real-time analytics and adaptive protection. Proactively assess your infrastructure, update policies, and embrace emerging technologies such as AI-driven threat detection to fortify your defenses.
Here are some tips to help futureproof your cloud security strategies:
- Regularly review and update your security protocols to address new threats.
- Integrate automated monitoring and incident response systems.
- Invest in next-generation security platforms that incorporate AI and machine learning.
- Continuously train your staff on emerging cybersecurity threats and best practices.
» Futureproof your data privacy by combining ISO 27001 and ISO 27701
The Role of AI and Automation
Artificial intelligence and automation revolutionize cloud security by enhancing threat detection, response times, and overall system resilience.
Automation further streamlines security operations, reducing manual intervention and human error.
These modern solutions offer dynamic, proactive protection against emerging cyber threats. At the same time, traditional methods often rely on static, rule-based systems that can struggle to keep pace with evolving attack techniques.
The table below compares traditional security methods with modern, automated solutions:
| Aspect | Traditional Security Methods | Modern, Automated Solutions |
|---|---|---|
| Threat detection | Rule-based, periodic scanning. | Real-time, AI-powered anomaly detection. |
| Response time | Manual intervention, slower response | Automated responses, immediate mitigation |
| Scalability | Limited by human resources | Highly scalable with cloud-native tools |
| Adaptability | Static policies and signatures | Dynamic, machine-learning-driven adaptation |
| Resource efficiency | High operational overhead | Optimized through automation and analytics |
| Integration | Often siloed, less cohesive | Seamlessly integrated across platforms |
This comparison underscores the shift toward intelligent, automated security practices that can keep pace with the evolving threat landscape in cloud environments.
» Learn more about AI's role in the future of cybersecurity
Regulatory and Compliance Forecasts
Future cloud security requirements will likely become more stringent as governments and industry bodies respond to the rising frequency and sophistication of cyber threats.
Here's a summary of potential cybersecurity compliance requirements:
| Regulation | Upcoming Changes | How Businesses Should Prepare |
|---|---|---|
| GDPR | Stricter data breach reporting rules | Enhance incident response plans and logging practices. |
| SOC 2 | Higher security audit standards | Conduct regular security audits and implement automated compliance tracking. |
| HIPAA | New guidelines for cloud-based healthcare data | Encrypt all sensitive healthcare data in transit and at rest. |
| ISO 27001 | Expansion of risk management controls | Implement continuous risk assessment and monitoring tools. |
» Learn about the merits of adopting ISO 27001/SOC 2
Organizations must adapt to evolving data privacy laws, enhanced breach notification mandates, and a greater emphasis on continuous monitoring and reporting.
Staying ahead of these changes means building flexible compliance frameworks that quickly adjust to new standards and incorporate emerging technologies for real-time risk management.
Recommendations for staying ahead of regulatory changes:
- Invest in automated compliance management systems that integrate with your security infrastructure.
- Regularly review and update internal policies to align with new and emerging standards.
- Establish robust audit trails and real-time reporting capabilities.
- Engage in proactive risk assessments and implement adaptive security controls that can respond to evolving regulatory demands.
Secure Your Cloud With GRSee Consulting
GRSee Consulting provides specialized cloud security services to help organizations protect their cloud environments and maintain regulatory compliance. We provide penetration testing to identify vulnerabilities before attackers exploit them and cloud security assessments to audit your cloud environment according to industry and vendor best practices.
GRSee’s tailored approach ensures that your organization stays ahead of evolving threats. By partnering with us, you gain access to industry-leading security expertise that helps you build a resilient cloud infrastructure, prevent data breaches, and comply with critical compliance frameworks such as SOC 2 and ISO 27001.
» Take control of your cloud security—contact GRSee today