Gray Box Pentest: Why This Hybrid Approach May Be Best
Secure your systems with gray box penetration testing, the hybrid solution for identifying vulnerabilities and improving your security defenses.
Published April 5, 2025.

The importance of cybersecurity cannot be overstated in a digital age where every organization is a potential target. With cyber threats at an unprecedented pace, no business is immune to potential attacks. In fact, the 2024 Verizon Data Breach Investigations Report highlights system intrusion as the leading cause of breaches, underscoring the need for proactive security measures to stay ahead of evolving threats.
Penetration testing is a proactive approach to identifying and mitigating vulnerabilities before they can be exploited. Among the various methods, gray box testing stands out as a hybrid approach, blending insights from black box (external) and white box (internal) testing.
» Don't leave security to chance! Start with GRSee today
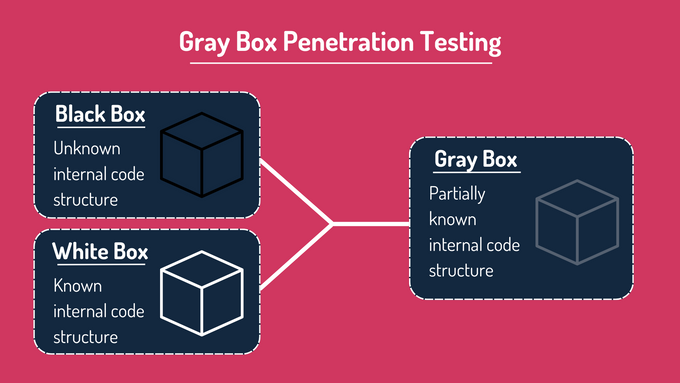
What Is Gray Box Penetration Testing?
Gray box penetration testing is a hybrid security assessment method that combines aspects of both black box and white box testing. It provides testers with partial knowledge of the system, such as login credentials or limited architectural details, allowing for a focused and realistic evaluation of vulnerabilities.
» Start at the beginning with different types of penetration tests
Gray Box vs. Black Box Testing
Black box testing evaluates system security from an outsider’s perspective, with no prior knowledge of the system's internals. While this approach is effective for identifying vulnerabilities that an external attacker might exploit, it often overlooks internal weaknesses due to its limited scope.
In contrast, gray box security testing offers partial system insights, enabling testers to focus on areas that an external attacker could target while also addressing internal vulnerabilities. This balance enhances the efficiency and depth of the testing process, making gray box testing more comprehensive than black box testing alone.
Gray Box vs. White Box Testing
White box testing grants testers complete access to system internals, including source code, configurations, and architecture. This level of transparency enables a thorough security assessment but can be time-consuming and resource-intensive.
Gray box testing provides a middle ground. Testers have enough information to simulate realistic attack scenarios without requiring full access to the system. This hybrid approach is less resource-intensive than white box testing while still uncovering critical vulnerabilities that might be missed in a black box evaluation.
Benefits of Gray Box Testing
- Efficient balance between internal and external testing: Gray box testing seamlessly blends internal knowledge with external attack methodologies, providing a unique and balanced approach. By combining these perspectives, organizations can efficiently focus on the most critical vulnerabilities.
- Cost-effectiveness: Compared to white box testing, gray box testing offers significant cost savings by requiring fewer resources and less time for in-depth analysis.
- Simulates real-world attacks: Gray box testing simulates realistic attack scenarios using partial insider knowledge. This approach helps evaluate how well critical security controls, such as authentication and access management, resist potential breaches.
» Want to learn more? Discover the different types of penetration tests
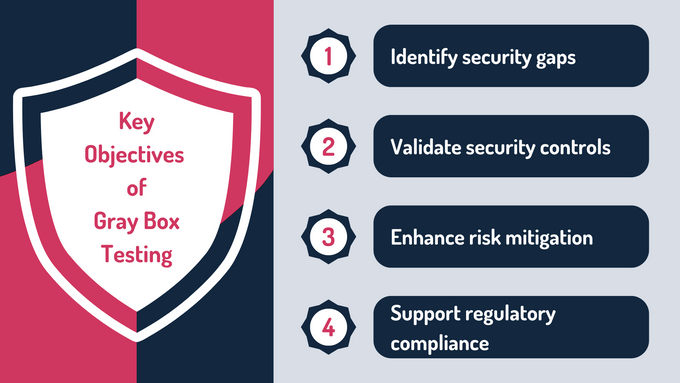
Key Objectives of Gray Box Testing
Gray box penetration testing is essential as it serves multiple objectives, combining the best of black and white box methodologies to uncover vulnerabilities efficiently. Its focus extends beyond detecting weaknesses by offering valuable insights to improve security and ensure compliance:
- Identify security gaps: Gray box pentesting pinpoints vulnerabilities such as misconfigurations, privilege escalation risks, and coding flaws, ensuring these gaps are addressed before exploitation.
- Validate security controls: By testing mechanisms like authentication, access controls, and session management, gray box security testing ensures these controls function as intended to protect sensitive data.
- Enhance risk mitigation: This method simulates realistic attack scenarios, enabling organizations to strengthen their defenses and improve response strategies for emerging threats.
- Support regulatory compliance: Gray box testing makes meeting standards like PCI DSS or HIPAA easier, as it validates compliance and provides essential documentation for audits.
The Gray Box Penetration Testing Process
Step 1: Planning and Scoping
The process of penetration testing begins by defining the scope of the test, including the systems, applications, or environments to be evaluated. This step ensures that the testing aligns with organizational objectives and complies with relevant regulations like PCI DSS or HIPAA.
Step 2: Reconnaissance and Vulnerability Identification
Testers gather information about the target environment, such as system configurations, exposed services, and known vulnerabilities. By leveraging partial system knowledge, they identify weak points that attackers could exploit.
Step 3: Exploitation and Impact Assessment
Testers attempt to exploit identified vulnerabilities to determine their potential impact on the system. This step helps evaluate how an attacker could compromise the environment, escalate privileges, or exfiltrate sensitive data.
Step 4: Reporting and Remediation Recommendations
The final step involves delivering a detailed report outlining the findings, potential risks, and remediation steps. This documentation is crucial for addressing vulnerabilities, strengthening security measures, and meeting compliance requirements.
» Confused about compliance? Compare traditional compliance methods and automation platforms
Challenges and Mitigation Strategies
1. Limited Internal Visibility
Gray box testing relies on partial knowledge, which can restrict testers from uncovering deeper vulnerabilities within the system that more educated attackers might find.
Here's what you can do:
- Grant scoped access: Provide controlled access to high-priority components, ensuring critical areas are evaluated without compromising the partial-knowledge approach.
- Leverage documentation: Share system architecture diagrams and technical documentation to aid testers in navigating the environment more effectively.
- Foster collaboration: Involve internal teams to bridge knowledge gaps and provide critical insights about hidden complexities.
2. Time Constraints
Strict deadlines in penetration testing can lead to incomplete assessments, compromising the thoroughness needed to identify vulnerabilities. Balancing efficiency and depth is a common challenge for teams under time pressure.
Here's what you can do:
- Adopt phased testing: Divide the testing process into manageable phases, prioritizing high-risk areas first while ensuring each phase is comprehensive and well-documented.
- Use automation tools: Automate routine tasks like vulnerability scanning to free up time for manual testing of critical systems.
- Plan for flexibility: Include buffer time in the testing schedule to handle unexpected findings or additional areas that may need attention.
3. Overlooked Context
Without proper collaboration, testers may miss essential system-specific details, such as operational nuances, workflows, or known vulnerabilities. This lack of context can lead to incomplete assessments and recommendations.
Here's what you can do:
- Encourage knowledge sharing: Conduct workshops or meetings with internal stakeholders to share insights into workflows, system behavior, and known risks.
- Document known issues: Provide testers with historical data on vulnerabilities or incidents to ensure focus on high-risk areas.
- Implement regular feedback loops: Establish frequent communication between testers and internal teams to refine the testing process and ensure all critical aspects are covered.
Tools and Techniques Used in Gray Box Pentesting
Gray box penetration testing combines automated tools and manual techniques to identify vulnerabilities effectively. With a diverse set of tools for different stages of the process, this approach provides a comprehensive assessment of system security.
1. Scanning and Reconnaissance
- Nmap: Used for network discovery and identifying open ports.
- Nessus: Conducts vulnerability assessments to uncover misconfigurations and potential risks.
- OpenVAS: Performs in-depth scans to identify vulnerabilities in networks and systems.
2. Application Testing
- Burp Suite: Detects web application vulnerabilities, including XSS, SQL injection, and session management issues.
- ZAP: Focuses on identifying common security flaws in web applications through active and passive scans.
- Postman: Facilitates API testing to ensure secure endpoints and proper configurations.
3. Code and Configuration Analysis
- SAST tools: When credentials are available, static application security testing (SAST) tools can be used for code reviews to identify insecure coding practices.
- Configuration review utilities: Analyzes system settings and configurations to detect potential security gaps.
4. Exploitation Frameworks
- Metasploit: Simulates exploits to test for vulnerabilities and assess system defenses.
- Cobalt Strike: Simulates advanced persistent threats (APTs) to evaluate incident response and defense mechanisms.
Integrating Gray Box Pentesting With Other Methods
The Benefits of Combining Gray Box Testing
Gray box testing combines partial internal knowledge with an external perspective for a balanced security approach. When paired with black box testing, which simulates an attacker's viewpoint, and white box testing, which analyzes code-level vulnerabilities, organizations gain a more comprehensive understanding of their security posture.
Measurable benefits include:
- Comprehensive coverage: This approach addresses vulnerabilities at every level, ensuring there are no gaps between external threats, system-level misconfigurations, and internal code flaws.
- Improved efficiency: Each method focuses on specific aspects, minimizing overlap while maximizing vulnerability detection.
- Enhanced resilience: Multi-layered testing helps organizations build stronger defenses against both targeted and widespread attacks.
- Regulatory compliance: Thoroughly assesses all aspects of security to meet the stringent requirements of standards like PCI DSS and HIPAA.
» Stay up to date with changing PCI DSS requirements
Potential Risks of Overlap
Overlapping testing methods can lead to redundant efforts and resource strain if not properly managed. Defining clear scopes and prioritizing tasks ensures efficient and focused assessments.
| Risk | Explanation | Mitigation | Example |
|---|---|---|---|
| Redundant Efforts | Unclear scope and objectives can lead to duplicate evaluations of vulnerabilities, wasting time and resources | Define clear scopes for each method to avoid duplication | Assign gray box testing to internal systems and black box testing to external vectors |
| Resource strain | Overlapping methodologies can overburden teams, delaying timelines and limiting focus on high-priority issues | Strategically allocate resources and use phased testing schedules | Start with black box testing, then prioritize deeper analysis with gray or white box methods |
Scenarios Where a Multi-Layered Approach Is Most Effective
Highly Regulated Industries
Industries like healthcare, finance, and retail face stringent regulatory requirements, such as PCI DSS or HIPAA. These sectors demand both detailed audits and real-world attack simulations to meet compliance standards and safeguard sensitive data. A combined approach enables:
- Thorough audits through white box testing for in-depth code and configuration reviews.
- Real-world simulations via black and gray box testing to identify exploitable vulnerabilities in live environments.
- Documentation alignment with compliance standards to demonstrate proactive security measures.
Organizations With Hybrid Infrastructures
Hybrid infrastructures, combining on-premises and cloud environments, introduce complexity and a larger attack surface. This scenario benefits greatly from a multi-layered approach by:
- Using gray box testing to evaluate interconnections between systems and simulate insider threats.
- Employing black box testing to explore external vulnerabilities, such as exposed endpoints or misconfigured access controls.
- Incorporating white box techniques for detailed analysis of APIs, configurations, and code for cloud-native components.
How GRSee Helps You With Gray Box Penetration Testing
At GRSee Consulting, we tailor gray box penetration testing to address the unique risks and environments of each business. Combining manual cyberservice expertise with advanced tools, we ensure thorough coverage across critical areas of your infrastructure while aligning strategies with regulatory frameworks like PCI DSS and GDPR. Our actionable insights help mitigate vulnerabilities effectively and enhance your overall security posture.
Beyond testing, GRSee integrates gray box vulnerability testing with broader security assessments for maximum impact. We also offer post-testing advisory services to help businesses address vulnerabilities and strengthen their defenses.
» Ready to simplify PCI DSS compliance? Contact GRSee today