How Unique Identifiers (UUIDs) Minimize Risk & Enhance Data Security
UUIDs play a pivotal role in bolstering security and maintaining data integrity within distributed systems, offering scalable, robust solutions to modern cybersecurity challenges
Published April 5, 2025.

The digital landscape is evolving at a breakneck pace, with organizations increasingly embracing distributed systems to manage their data. Due to this increasing reliance on such environments, the need for robust security measures has never been greater. Without the right safeguards, data breaches and operational risks can spiral out of control.
Universal Unique Identifiers (UUIDs) offer a practical and efficient way to enhance data security. Ensuring each piece of information is uniquely identifiable, UUIDs minimize the risk of duplication, collision, or unauthorized access. In this article, we'll explore how UUIDs work and why they are essential in modern data management
» Looking for an effective cybersecurity solution for your business? Contact us
What Is a UUID?
A Universal Unique Identifier (UUID) is a 128-bit number used to uniquely identify information in computer systems. Typically represented as a 32-character hexadecimal string, UUIDs are split into five groups separated by hyphens (e.g., 123e4567-e89b-12d3-a456-426614174000).
A 128-bit number can hold an extremely large range of unique values, and a 32-character hexadecimal string represents this number using a mix of numbers (0-9) and letters (A-F).
Differences Between UUIDs and Other Identifiers
- Serial numbers: Sequentially assigned numbers, unique within specific systems but lack global uniqueness. They rely on a central authority for generation.
- Auto-incremented IDs: Database-generated identifiers that automatically increase as records are added. They are limited to uniqueness within a specific database or system.
- Natural keys: Derived from existing data like social security numbers or email addresses. While unique within a domain, they are not globally unique.
To better understand how UUIDs compare with other common identifiers, let's take a look at the table below for a clear breakdown of their key attributes.
| Factor | UUIDs | Serial Numbers | Auto-incremented IDs | Natural Keys |
|---|---|---|---|---|
| Uniqueness | Globally unique | Unique within a system | Unique to a database | Unique in a domain |
| Generation | Uses time, randomness, or hashing | Sequentially assigned | Auto-incremented by the database | Derived from existing data |
| Decentralization | No central authority is needed | Requires central assignment | Database-dependent | Needs domain-level validation |
| Collision Risk | Extremely low collision probability | Higher in shared systems | Possible in multi-database setups | Higher due to duplication risks |
| Scalability | Ideal for distributed systems | Limited for cross-systems | Restricted to its database | Bound to its context or domain |
5 Types of UUIDs and Their Use Cases
UUIDs are created using various mechanisms to ensure uniqueness, including timestamps, random numbers, and, in some cases, hardware-specific information (e.g., MAC addresses). Here are the different versions of UUIDs and how they're created:
UUIDv1: Time-Based
Used for distributed systems that benefit from UUIDv1 for time-ordered identifiers, such as log entries across servers. It ensures uniqueness by combining timestamps and MAC addresses, though it may expose hardware details.
UUIDv2: User-Specific
Operating systems can use UUIDv2 for user-specific resource identification, embedding user data alongside timestamps. Limited adoption and secure alternatives often make this less common. They are similar to UUIDv1 but include additional information such as user identifiers.
UUIDv3: Namespace-Based (Deterministic)
Useful for generating consistent identifiers, such as unique URLs in content management systems. UUIDv3 ensures deterministic results as it is generated using a hash of a namespace identifier (e.g., a URL) and a name, ensuring the same inputs always produce the same UUID.
UUIDv4: Randomized
Widely used for scenarios like session or transaction identifiers. Its reliance on random number generation provides robust uniqueness and minimizes collision risks.
UUIDv5: Secure Namespace-Based
Ideal for sensitive resources such as APIs or digital assets, UUIDv5 uses SHA-1 hashing for secure, deterministic identifiers, enhancing collision resistance and overall security.
Common Applications of UUIDs in Software Systems
UUIDs are already part of real-world software systems. Their ability to provide unique identifiers across diverse environments makes them integral to modern development. The most common uses in modern software systems include:
- Database keys: In distributed databases, UUIDs function as primary keys, solving the challenge of ensuring unique identifiers across multiple systems without a central coordinator.
- Session tokens: Web applications utilize UUIDs to uniquely identify user sessions, enhancing session tracking and improving application security.
- API identifiers: Many RESTful APIs depend on UUIDs to uniquely tag resources, enabling consistent and reliable communication between services.
- File naming: UUIDs ensure unique file names, eliminating conflicts in file storage systems and streamlining file management processes.
- IoT devices: The Internet of Things (IoT) leverages UUIDs to distinguish devices, allowing seamless recognition and communication within vast networks of connected devices.
UUIDs not only ensure secure and efficient data management across distributed systems but also play a role in achieving compliance with global standards, including PCI DSS, and COSO.
» Stay up to date with changes in PCI DSS requirements
Example Usage of UUIDs
An e-commerce store utilizes UUIDs to enhance security and efficiency. A UUIDv4 is used to generate secure, unique session IDs for user interactions, while a UUIDv1 ensures seamless tracking of product updates across distributed systems. Additionally, a UUIDv5 creates consistent identifiers for product URLs or marketing campaigns, ensuring deterministic generation.
How UUIDs Strengthen Data Security and Integrity
UUIDs play a pivotal role in bolstering security and maintaining data integrity within distributed systems, offering scalable, robust solutions to modern cybersecurity challenges.
Risk Mitigation in Distributed Systems
UUIDs are essential for managing data in distributed systems. They offer decentralized ID generation that eliminates the need for central coordination. This approach prevents collisions and bottlenecks, enabling seamless operations in systems like global e-commerce platforms, where orders must be synchronized across regions without conflict.
Their scalability makes UUIDs ideal for cloud-based applications and microservices architectures, allowing organizations to grow without risking data conflicts. Additionally, UUIDs enhance data integrity by preventing overwrites and ensuring consistency, which is critical in environments like financial databases or IoT ecosystems. These features make UUIDs a cornerstone of efficient and reliable data management.
» Find out more about ensuring security in a cloud infrastructure
Enhancing Security Compared to Traditional Identifiers
- Obfuscation: UUIDs, particularly UUIDv4, are inherently difficult to guess or predict, reducing risks tied to identifier-based attacks.
- Reduced attack surface: High entropy and a vast keyspace make UUIDs highly resistant to brute-force attacks, drastically lowering the probability of unauthorized access.
- Replay attack prevention: When used as session tokens or transaction IDs, UUIDs ensure each session or transaction is uniquely identifiable, mitigating the risk of replay attacks.
UUIDs provide a scalable, collision-resistant solution for distributed systems, ensuring data integrity, enhanced security, and seamless operations without central coordination.
» Make sure you understand risk assessment and what's involved in the risk assessment process
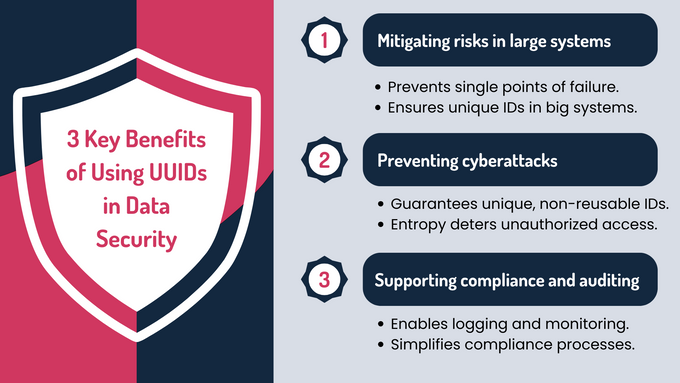
Benefits of UUIDs in Data Security
1. Mitigating Risks in Distributed Systems
UUIDs enable decentralized ID generation across systems without requiring a central authority, eliminating single points of failure. Their strong collision resistance ensures unique identifiers even in environments generating billions of IDs, enhancing reliability and security.
2. Strengthening Defenses Against Cyberattacks
UUIDs reduce the risk of replay attacks by ensuring each identifier is unique and non-reusable. Their high entropy and randomness provide critical protection against brute-force attempts and unauthorized access.
» Concerned about cyberattacks? Consider professional cyberservices
3. Facilitating Compliance and Traceability
UUIDs act as globally unique identifiers that enhance traceability across systems, simplifying compliance and auditing. They enable precise logging and monitoring, essential for meeting regulatory requirements and improving data security practices.
» Need help with compliance? Read our comparison of traditional compliance methods and platforms
Integrating UUIDs With Other Security Measures
UUIDs can be seamlessly integrated with encryption, hashing, and tokenization to strengthen overall system security:
- Encryption prevents unauthorized interception and ensures that UUIDs remain confidential when transmitted over insecure channels, such as during financial transactions.
- Hashing UUIDs before storage further enhances security by rendering them unreadable in case of database or log compromises, ensuring identifiers remain protected.
- In tokenization systems, UUIDs substitute for sensitive data like credit card numbers or personal identifiers, reducing the risk of breaches.
This method securely stores actual sensitive data in isolated environments while using UUIDs for external operations, a common practice in payment systems to meet compliance requirements like PCI DSS. Together, these integrations make UUIDs vital components in multi-layered security architectures.
» Interested in reaching PCI DSS compliance? Take a look at these success factors and our guide to building a robust PCI DSS security strategy
Example Systems
- OAuth systems: UUIDs function as unique client IDs or access tokens, enabling precise identification and authorization of users or devices in secure authentication flows.
- Payment systems: UUIDs are used to tokenize sensitive financial data, such as credit card numbers, preventing direct exposure of the data and reducing the risk of theft or misuse.
Risks and Limitations of UUIDs in Data Security
UUIDs are powerful tools in data security, but their use comes with certain risks and limitations. Understanding these challenges and employing effective mitigation strategies ensures optimal performance and security in large-scale systems.
1. Collision Risk
A collision occurs when two systems generate the same identifier, leading to potential conflicts or data inconsistencies.
Although the probability of UUID collisions is extremely low, it is not zero and can undermine systems relying on unique identifiers. This risk is particularly relevant in systems generating a massive number of IDs rapidly.
Mitigation strategies include using UUIDv1 (time-based) or UUIDv4 (randomized), which leverage timestamps or random numbers to ensure uniqueness.
2. Performance Implications in Databases
UUIDs, especially as primary keys, can degrade database performance due to their random nature causing fragmentation and slower queries. Time-based UUIDs introduce order to reduce fragmentation while pre-sorting or custom indexing strategies can optimize database efficiency.
3. Storage Overhead
UUIDs are longer than traditional identifiers, resulting in higher storage demands in large datasets. Compression techniques or alternative encoding methods, like base64, can reduce the storage footprint while preserving the advantages of UUIDs.
For example, a standard UUID is 36 characters, but base64 encoding reduces it to 22, saving space in storage-heavy applications.
» Looking to boost your cybersecurity? Learn about the CIA triad
Support Effective UUID Implementation Today
Universal Unique Identifiers (UUIDs) offer a powerful and versatile solution for minimizing risk and enhancing data security across a wide range of applications. From preventing primary key collisions and simplifying distributed systems to strengthening data anonymization and improving traceability, the benefits are clear. By embracing the use of UUIDs, organizations can significantly reduce the potential for data breaches, improve data integrity, and streamline various processes.
» Ready to boost your organization's security? Contact us to learn more