How SOC 2 Type 2 Strengthens Your Security Posture: A Full Guide
The growing thread of cybercrime has become a significant concern for businesses worldwide. As cybercriminals continue to evolve, the need to protect your organization's data has never been more critical.
Published April 5, 2025.

Reports from Cybercrime Magazine, estimate that cybercrime could cost the world $10.5 trillion annually by 2025, up from $3 trillion in 2015. Additionally, IBM highlights that data breaches have drastically surged, with today's average data breach cost reaching an all-time high of $4.88 million. This reality shows the critical need for you to adopt robust security measures and compliance frameworks to protect sensitive data and mitigate risks.
One of the most effective ways to strengthen your organization’s security posture is through security auditing and reporting compliance frameworks such as SOC 2 Type 2, demonstrating your commitment to maintaining high standards of information security and systematically identifying vulnerabilities, implementing appropriate controls, and ensuring ongoing protection against cyber threats.
» Let the experts handle your SOC 2 Type 2 compliance with our startup and enterprise services
What Is SOC 2 Type 2?
SOC 2 Type 2 is a auditing and reporting framework developed by the American Institute of CPAs (AICPA) to evaluate an organization’s controls over a specified period, typically 3 to 12 months. It is tailored for service organizations that handle sensitive information, assessing their ability to protect client data through rigorous security, availability, processing integrity, confidentiality, and privacy measures.
Unlike compliance frameworks like HIPAA, which focuses on healthcare, or PCI-DSS, which targets payment card data security, SOC 2 Type 2 has a broader scope and applies to many industries. Its primary focus is on the effectiveness of the controls implemented over time, providing a more comprehensive evaluation of an organization’s security posture.
For organizations handling sensitive data, particularly those in industries like finance, healthcare, and technology, SOC 2 Type 2 is critical.
SOC 2 type helps your organization to:
- Safeguard client information
- Meet industry-specific regulatory requirements
- Reduce the risk of data breaches
- Enhance overall business resilience
» Learn more about what is SOC 2
The Difference Between SOC 2 Type 1 and Type 2
SOC 2 Type 1
SOC Type 1 provides a snapshot of an organization’s controls at a specific point in time. It evaluates whether the necessary controls are in place but does not evaluate how effectively they operate over time. This type of report is typically used by startups or smaller organizations that are starting their compliance journey.
SOC 2 Type 2
SOC 2 Type 2 evaluates control effectiveness over 3 to 12 months, testing consistency and reliability. This offers greater assurance to clients, especially in industries like finance and healthcare, which often require SOC 2 Type 2 to demonstrate ongoing compliance and security.
Choosing the appropriate SOC 2 type depends on your organization’s specific needs, regulatory requirements, and the level of assurance required by clients and partners.
Benefits of SOC 2 Type 2 Compliance
- Building trust: SOC 2 Type 2 compliance significantly boosts trust by demonstrating a strong commitment to security. This trust is crucial in industries like finance, healthcare, and technology, where data security is critical. The framework differentiates organizations, making them more credible and appealing to clients and stakeholders.
- Gaining a competitive edge: SOC 2 Type 2 compliance provides a competitive edge. Companies that follow the framework are often preferred in B2B environments, where clients need assurance that their data is secure. It acts as proof of an organization’s ability to protect sensitive information, opening doors to new business opportunities and strengthening customer loyalty.
- Driving operational efficiency: The compliance process also drives operational efficiency. By implementing and monitoring security controls, organizations identify and correct inefficiencies, enhancing both security and overall operations. This continuous improvement reduces risks, optimizes resource use, and builds resilience against emerging threats.
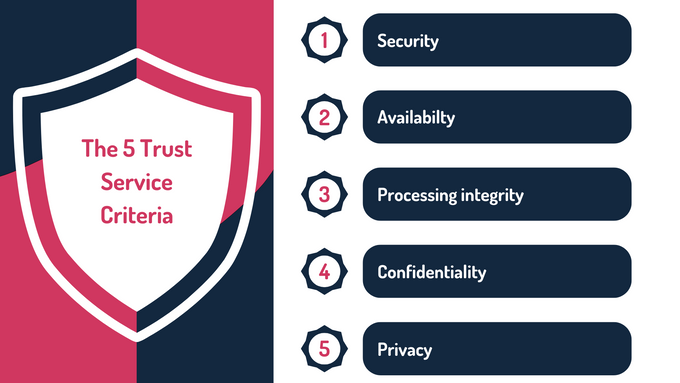
The Five Trust Service Criteria
- Security: Security is the core criterion for all SOC 2 audits and is mandatory. It examines safeguards against unauthorized access, both physical and logical, including firewalls, intrusion detection systems, and multi-factor authentication (MFA). These controls are vital for reducing the risk of cyberattacks and protecting sensitive data.
- Availability: The availability criterion ensures that systems are operational and accessible according to agreed service level agreements (SLAs). It evaluates backup procedures, incident response, and disaster recovery plans to maintain service continuity even during disruptions.
- Processing integrity: Processing integrity guarantees that systems process data completely, accurately, and timely. This involves preventing unauthorized data modifications, essentially ensuring reliable and consistent service delivery. It is especially important for organizations providing critical services to clients.
- Confidentiality: Confidentiality protects sensitive information from unauthorized access and disclosure. This includes encryption, access controls, and data masking to secure confidential data, such as financial records. Maintaining confidentiality builds client trust and ensures regulatory compliance.
- Privacy: The privacy criterion mandates that personal information is handled according to relevant laws and regulations, such as GDPR or CCPA. It covers the collection, retention, and disposal of personal data, ensuring that organizations manage personal information responsibly and avoid legal penalties.
Essential Security Controls in SOC 2 Type 2
SOC 2 Type 2 compliance focuses on key security controls that are essential for strengthening an organization's security. These controls protect sensitive data, limit access to authorized users, and prepare the organization to handle security incidents effectively.
Security Controls
Access Controls
- Manage and restrict access to sensitive business data to authorized personnel only.
- Implement role-based access, multi-factor authentication (MFA), and regular access reviews to prevent unauthorized access and ensure data confidentiality.
Encryption
- Protect data from unauthorized individuals by encrypting it both in transit and at rest.
- Ensure that sensitive information remains secure and unreadable even if intercepted or accessed by unauthorized parties.
Monitoring and Logging
- Track user activities and detect events in real time to respond to security incidents promptly.
- Implement detailed logging of user actions and system events to identify suspicious activity and enable quick responses to potential threats.
Incident Response Plan
- Develop and implement a set of procedures to address security breaches or incidents effectively.
- Train staff on their roles during incidents, ensuring rapid recovery, minimizing downtime, and reducing potential damage.
Change Management
- Establish controls to review and authorize all changes to systems and processes, preventing the introduction of vulnerabilities.
- Ensure that security measures remain effective over time through formal change request procedures and impact assessments.
Physical Security
- Protect physical access to critical infrastructure, such as data centers, to prevent unauthorized access.
- Implement security measures like biometric access controls, surveillance cameras, and secure facilities, especially for organizations not exclusively operating in the cloud.
Data Backup and Recovery
- Ensure regular data backups and implement recovery processes to maintain data availability in case of loss or corruption.
- Support business continuity by regularly testing recovery procedures and securely storing backup data.
Vendor Management
- Manage and assess third-party vendors to ensure they meet the organization’s security standards.
- Reduce the risk of breaches by ensuring that vendors with access to sensitive data adhere to stringent security requirements through regular assessments and monitoring.
Staying Compliant: The Lifecycle of SOC 2 Type 2 Reports
A SOC 2 Type 2 report is typically valid for 12 months, after which a new audit is required to ensure compliance.
To keep your compliance up to date and ensure your security remains strong, it is important to take a few proactive steps:
- Engage in regular monitoring: Continuously monitor and review all security controls to ensure they remain effective and aligned with SOC 2 standards. This process helps identify and address potential issues before they escalate into significant risks.
- Prepare for compliance audits: Conduct periodic internal audits to assess the effectiveness of implemented controls and to ensure the organization is ready for the next external audit. These internal checks help to maintain a high level of preparedness and reduce the likelihood of surprises during the formal audit process.
- Update documentation and processes: Regularly update policies, procedures, and documentation to reflect any changes in the organization’s environment or regulatory requirements. This ensures compliance and allows the organization to swiftly adapt to new challenges in the compliance landscape.
By adopting these practices, you can sustain your business' SOC 2 Type 2 compliance over time, ensuring ongoing protection of sensitive data and maintaining a strong security posture.
GRSee's Role in SOC 2 Type 2 Compliance
At GRSee, our team of experts is dedicated to helping you achieve and maintain SOC 2 Type 2 compliance, ensuring your security posture is strong and your operations meet industry standards. Here's how we can help:
Advisory services: We begin with a gap analysis to identify areas for improvement, followed by a detailed work plan. Our experts assist with implementing the necessary controls, ensuring your operations align with SOC 2 requirements.
Assurance services: After the observation period, our independent auditors conduct the external audit, reviewing all evidence and documentation to confirm that your organization meets SOC 2 Type 2 standards.
vCISO services: Our Virtual Chief Information Security Officer (vCISO) services provide ongoing compliance support, including continuous monitoring, risk assessments, and vendor management, ensuring your organization remains audit-ready and secure.