How to Conduct Thorough PCI DSS Gap Assessments & Minimize Risk
Learn how to conduct a thorough PCI DSS gap assessment to identify compliance gaps and mitigate security risks, helping your organization maintain a strong security posture.
Updated April 10, 2025.

Navigating the complexities of PCI DSS compliance can be challenging for any organization. However, with a structured approach, you can identify gaps early and take action to address them.
By using a clear, risk-based strategy and aligning your compliance efforts with broader security initiatives, you ensure not only compliance but also a stronger security posture. Regular assessments and prioritizing remediation efforts will safeguard your systems as you scale.
» Meet PCI DSS requirements easily: Contact us
How a PCI DSS Gap Assessment Strengthens Cybersecurity
A gap analysis or assessment is a tool or process that identifies gaps between an organization's current security posture and the requirements of the Payment Card Industry Data Security Standard (PCI DSS).
» Need more help? Here's how to build a robust PCI DSS security strategy
1. Enhanced Overall Security Posture
A PCI DSS gap assessment improves an organization’s security practices by identifying and addressing gaps, allowing the organization to improve and add missing controls as needed.
For example, it may reveal the use of default passwords on system components, a PCI DSS violation that requires corrective action.
Strengthening security across the business network not only reduces risks but also enhances the organization's reputation, attracting partners and customers who prioritize strong cybersecurity practices.
2. Cost Reduction
By identifying areas of over-compliance or unnecessary spending, a gap assessment can uncover cost-saving opportunities. A thorough gap assessment can identify areas where existing security measures exceed PCI DSS requirements.
While PCI DSS mandates specific and mandatory tools and controls, some organizations may implement additional, non-required security tools or processes. Identifying these areas of over-compliance can free up resources that can be strategically reinvested in other security enhancements or business initiatives.
» Learn more: Here are the benefits of PCI DSS compliance
PCI DSS Gap Assessment vs. PCI DSS Audit
| Aspect | PCI DSS Gap Assessment | PCI DSS Audit |
|---|---|---|
| Objective | Identifies gaps and areas of non-compliance before a formal audit. Helps organizations proactively address gaps. | Determines if an organization meets all PCI DSS requirements and can officially certify compliance. |
| Conducted By | Internal security teams or, preferably, by an external Qualified Security Assessor (QSA). While no official certification is issued after the assessment, engaging a QSA that's separate from the actual auditor but from the same company offers valuable expertise without conflict of interest and can provide a more objective evaluation of your security posture. | A Qualified Security Assessor (QSA) who follows PCI SSC guidelines to certify compliance. |
| Timing | Performed before an official audit or as part of ongoing security improvements. Can be conducted at any time to assess readiness. | Takes place at the end of a compliance cycle or when an organization seeks PCI DSS certification. |
| Outcome | A detailed report identifying areas where current security controls and practices fall short of PCI DSS requirements. While the gap assessment itself primarily focuses on identifying these discrepancies, the findings could serve as the foundation for developing a comprehensive risk remediation plan. | Determines whether the organization passes or fails PCI DSS compliance and issues an official Report on Compliance (RoC) or Self-Assessment Questionnaire (SAQ) validation. |
| Flexibility | Iterative and adjustable, allowing organizations to improve security posture gradually before facing a formal audit. | Rigid, with strict pass/fail criteria. Organizations must meet all requirements at the time of the audit to achieve compliance. |
» Keep these PCI DSS myths in mind
Common PCI DSS Challenges in Gap Assessment
1. Access Control
- Challenge: Legacy systems often run on outdated software with unsupported access control mechanisms.
- Impact: These outdated systems make it difficult to update security measures and ensure PCI DSS compliance.
2. Network Segmentation
- Challenge: Properly defining the Cardholder Data Environment (CDE) and ensuring network segmentation is a complex task.
- Impact: If segmentation controls aren't properly implemented, an entire corporate network, including laptops, can fall within the scope of PCI, creating a significant compliance burden
3. Monitoring
- Challenge: Handling large volumes of data logs and network traffic can be overwhelming without the right monitoring tools.
- Impact: Without effective monitoring, detecting anomalies becomes difficult, and potential threats could go unnoticed.
» Avoid these PCI-DSS pitfalls
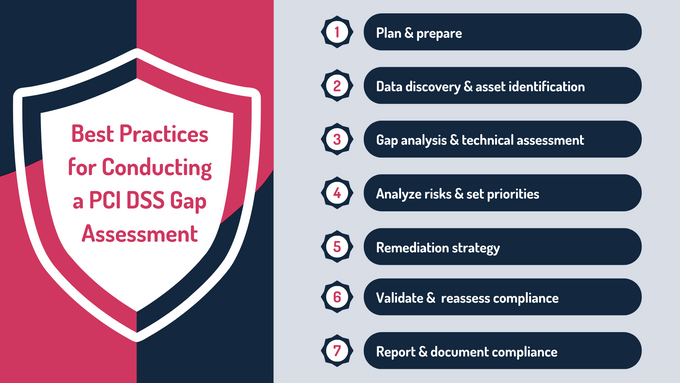
1. Plan & Prepare
A well-structured approach is essential for a successful PCI DSS gap assessment. Follow these key steps to ensure thorough preparation:
- Define the scope: Identify cardholder data (CHD) flows, systems, and networks within the PCI DSS scope.
- Assemble a cross-functional team: Include IT, security, compliance, and business representatives.
- Align expectations: Conduct stakeholder meetings to establish timelines and methodologies.
- Gather documentation: Collect network diagrams, policies, and asset inventories.
- Engage experts if needed: Consult a Qualified Security Assessor (QSA) or internal auditor.
- Secure leadership support: Ensure resource allocation for a smooth assessment.
- Develop a structured plan: Outline objectives, responsibilities, and deadlines to stay on track.
2. Data Discovery & Asset Identification
A thorough data discovery exercise ensures all sensitive cardholder data (CHD) is accounted for and properly secured. Follow these steps:
- Conduct data discovery: Use automated tools to locate unsecured CHD across shared drives, databases, and applications.
- Identify in-scope assets: Include systems, networks, storage, and third-party vendors handling CHD.
- Review payment flow diagrams: Track where CHD is stored, processed, or transmitted.
- Validate encryption & access controls: Ensure proper encryption, key management, and access controls are in place for sensitive data.
- Ensure vendor compliance: Verify that all service providers comply with PCI DSS requirements.
- Update asset inventory: Maintain an up-to-date inventory that aligns with PCI DSS scope.
3. Gap Analysis & Technical Assessment
This step evaluates your current security posture and identifies specific areas for improvement. Complete the following:
- Conduct detailed assessment: Perform assessments against each PCI DSS requirement (v4.0.1).
- Conduct scans & testing: Use vulnerability scans, penetration testing, and configuration reviews on in-scope systems.
- Analyze security practices: Review encryption practices, firewall rules, access controls, and monitoring mechanisms.
- Identify gaps: Pinpoint weaknesses in incident response, risk assessment, training, and third-party compliance.
- Document findings: Classify gaps with severity ratings (high, medium, low).
- Validate compensating controls: Check for compensating controls to mitigate compliance gaps.
- Engage system owners: Verify risk levels and assess the feasibility of remediation.
» Read more: Vulnerability scan vs. penetration test
4. Analyze Risks & Set Priorities
Evaluating risks helps you focus on remediation efforts on the most critical vulnerabilities. Follow these steps:
- Evaluate gaps: Analyze the impact and compliance requirements of identified gaps. Evaluating and prioritizing only gives you a roadmap to fix all gaps in the most efficient way.
- Classify gaps: Categorize gaps into policy/process, technical vulnerabilities, or vendor-related issues.
- Prioritize remediation: Focus on high-risk vulnerabilities such as unencrypted data, weak authentication, and network misconfigurations.
- Develop a remediation roadmap: Include short-term (quick fixes), mid-term (policy improvements), and long-term (infrastructure upgrades) actions.
- Align with business risk tolerance: Consider your organization's risk tolerance and regulatory obligations in your prioritization.
5. Remediation Strategy
This step involves applying corrective measures to address gaps and enhance your security posture. Follow these steps:
- Create a remediation plan: Assign tasks, deadlines, and responsible teams to ensure action on identified gaps.
- Implement security measures: Apply patch management, encryption enforcement, access control restrictions, and firewall optimizations.
- Update policies & documentation: Ensure all policies, procedures, and documentation reflect new compliance measures.
- Train employees: Educate employees on PCI DSS best practices, secure handling of CHD, and incident response protocols.
- Strengthen third-party contracts: Ensure all vendors meet PCI DSS standards.
- Conduct follow-up testing: Validate corrective actions and assess their effectiveness.
6. Validate & Reassess Compliance
After remediation, ensure all gaps are closed and compliance is achieved through reassessment. Follow these steps:
- Perform post-remediation assessment: Reassess systems to ensure all gaps have been closed.
- Conduct re-scans & audits: Perform internal scans, security control reviews, and audits.
- Verify encryption & access controls: Confirm that encryption configurations, logging mechanisms, and authentication controls meet PCI DSS standards.
- Reassess vendor compliance: Ensure that all service providers are still compliant with PCI DSS.
- Generate evidence for audits: Create supporting documentation for compliance audits.
- Conduct a pre-audit self-assessment: If necessary, use a PCI DSS SAQ or engage a QSA for external validation.
7. Report & Document Compliance
Once the assessment and remediation are complete, ensure proper documentation for compliance validation. Follow these steps:
- Compile a gap assessment report: Document findings, remediation actions, and the overall compliance status.
- Provide executive & technical summaries: Offer an executive summary for leadership and detailed technical information for IT/security teams.
- Document policies & controls: Include policies, risk assessments, and control implementations as evidence for compliance validation.
- Submit required reports: Complete and submit SAQ or ROC if applicable.
- Establish ongoing monitoring: Set up periodic audits, automated security scans, and continuous improvement initiatives.
- Maintain a compliance roadmap: Ensure long-term adherence to PCI DSS standards with an ongoing roadmap.
» Learn more about the PCI security standards
Methodologies for Performing a Gap Analysis
PCI DSS Requirements and Testing Procedures v4.0.1
- This document provides a structured approach to assessing PCI DSS compliance by evaluating security controls through documentation reviews, personnel interviews, and system configuration assessments.
- It ensures consistency across audits, helping organizations gain a clear understanding of their compliance posture.
Customized Approach Objectives
- PCI DSS v4.0.1 introduces a customized approach, allowing organizations to meet compliance requirements in a way that suits their unique environment.
- It requires additional documentation and justification, enabling compliance through alignment with industry standards while ensuring strong security governance.
Risk Assessment Methodologies
- Risk assessment frameworks like ISO 27005 and NIST SP 800-30 provide structured methods for identifying, evaluating, and mitigating risks within PCI DSS scope.
- PCI DSS v4.0.1 encourages targeted risk assessments, helping organizations implement security measures aligned with their risk exposure for a more efficient compliance process.
Penetration Testing Methodologies
- Penetration testing methodologies like OSSTMM and OWASP provide guidelines for identifying vulnerabilities through controlled attacks, using both manual and automated testing.
- PCI DSS mandates internal penetration testing to validate segmentation controls, uncover misconfigurations, and strengthen security defenses.
» Here's what you should know before hiring a risk assessment provider
Best Practices for Maintaining an Updated PCI DSS Compliance Status
1. Stay Informed Through Continuous Cybersecurity Education
Organizations should promote ongoing professional education by following cybersecurity news sites, podcasts, and blogs. Staying updated on emerging threats, evolving compliance requirements, and industry best practices enables security teams to anticipate risks and adjust security strategies accordingly. Continuous learning helps organizations stay ahead of cyber threats and align PCI DSS controls with the latest security advancements.
2. Integrate PCI DSS into Business-as-Usual (BAU) Processes
PCI DSS requirements should be seamlessly integrated into daily operations to ensure continuous compliance. Any system changes, network updates, or policy modifications must be assessed for compliance before implementation. Regular monitoring, failure response, and security control reviews help detect and address non-compliance proactively. By embedding PCI DSS into routine workflows, organizations reduce risk and maintain compliance effortlessly.
3. Continuously Validate PCI DSS Scope
As IT environments grow and evolve, frequent reassessment of PCI DSS scope is essential. Organizations should update data flow diagrams, identify all cardholder data systems (CDE), and ensure proper security controls are in place. Scope validation should be conducted at least annually or after significant system changes, while service providers should review their scope every six months. This prevents overlooked systems and ensures compliance coverage remains accurate.
4. Establish a Formal Change Management Process
A structured change management framework ensures that all new hardware, software, and configurations undergo security impact assessments, vulnerability scans, and compliance testing before deployment. Organizations must update security policies, documentation, and controls to reflect these changes, ensuring compliance is maintained even in fast-evolving IT landscapes.
» Discover the key success factors of PCI DSS compliance
How GRSee Consulting Supports Your PCI DSS Compliance Journey
GRSee Consulting guides you through the entire PCI DSS process, from conducting a gap analysis to securing final certification. Our team of certified QSAs leverages extensive knowledge of PCI DSS requirements to assess your organization's compliance landscape. GRSee’s tailored approach minimizes friction, clarifies roles, and ensures you maintain continuous compliance, even as your business evolves.
By working closely with you, we help develop streamlined programs that adapt to your needs, ensuring long-term security and minimizing risks along the way.
» Looking to achieve PCI DSS compliance? Contact us to explore our solutions