What Is Red Team Security Testing? A Comprehensive Guide
Discover how red team security testing uncovers hidden vulnerabilities. Strengthen your defenses with PCI DSS, ISO 27001, and SOC 2 compliance.
Published May 18, 2025.

Cybersecurity threats evolve daily. You need a strategy that exposes gaps in your defenses before malicious attackers do. Red team security testing is designed to uncover emerging cybersecurity vulnerabilities by simulating realistic adversarial tactics, techniques, and procedures.
This simulated approach helps ensure that your response capabilities, detection tools, and internal processes work effectively when an actual attack occurs.
» Uncover cybersecurity vulnerabilities through expert-guided penetration testing
What Is Red Team Security Testing?
Red team security testing involves a group of ethical hackers attacking an organization’s network, systems, and even physical premises (if within scope) using stealthy, carefully planned methods.
These professionals collaborate to exploit potential weaknesses, then relay their findings to the organization so it can address security flaws and improve its overall posture.
In contrast, traditional penetration testing or vulnerability assessments typically focus on specific systems or applications. They are often carried out by a single tester with a narrower scope. Red teaming goes further, involving multiple team members who brainstorm and coordinate attacks from start to finish. This broader, more collaborative approach is more resource-intensive than a standard penetration test.
» Learn more about penetration testing in cybersecurity
Primary Goals and Alignment With Broader Security Strategies
Red team assessments strive to:
- Identify flaws in systems, processes, and technology before cybercriminals do.
- Test the response capabilities of your blue team and detection tools.
- Enhance overall security posture by showcasing weak spots that require immediate attention.
On a broader scale, this process aligns with your more extensive risk management and governance strategy. If you can detect and remediate vulnerabilities early, you maintain better business continuity and protect sensitive data more effectively.
Which Organizations Benefit Most?
While all industries can gain from red team testing, financial institutions, healthcare facilities, and retail chains see exceptionally high value. They handle large volumes of sensitive data, making them prime targets for attackers. Red teaming helps these organizations quickly pinpoint and address critical blind spots—whether technical, human, or procedural.
Regulatory Alignment
Red team security assessments readily align with compliance requirements for standards such as PCI DSS, ISO 27001, and SOC 2:
- PCI DSS mandates regular penetration testing and vulnerability scans if you store, process, or transmit cardholder data.
- ISO 27001 contains clauses (e.g., A.12.6.1) addressing technical vulnerability management.
- SOC 2 (notably CC6.8) requires identifying and remediating security weaknesses.
Carrying out a thorough red team engagement helps you meet these compliance requirements by actively testing and improving your security controls.
» Compare the benefits and drawbacks between SOC 2 and ISO 27001
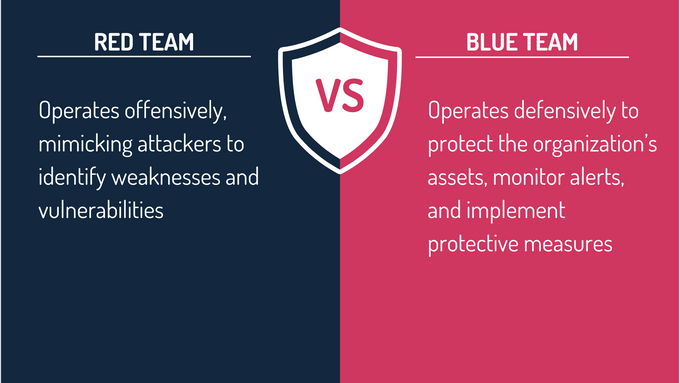
Red Team vs. Blue Team
Red team operates offensively, mimicking attackers to identify weaknesses and vulnerabilities. In contrast, blue team defends the organization’s assets, monitors alerts, and implements protective measures.
Both require:
- Meticulous attention to detail.
- Familiarity with penetration testing tools.
- Risk assessment and incident response expertise.
- Up-to-date knowledge of new attack methods.
Here is a quick snapshot:
| Red Team | Blue Team |
|---|---|
| Offensive security that simulates adversaries | Defensive security that responds to the attack |
| Uses every tool and tactic possible | Uses data from alerts and forensics |
| Brainstorms creative exploits as a group | Focuses on detection, analysis, and defense |
Key Red Team Methodologies and Tactics
Popular Frameworks
- MITRE ATT&CK: Red Teams often move beyond OWASP ZAP and rely on advanced methodologies for thorough web app assessments. This framework structures threat modeling and attack analysis. By mapping behaviors to the MITRE ATT&CK matrix, you get a clear picture of how different adversaries might act.
- NIST: Renowned for its broad applicability, the National Institute of Standards and Technology (NIST) cybersecurity framework helps organizations of all sizes build robust, flexible security programs.
- PCI DSS penetration test methodology: This standard is crucial if you handle payment card data, guiding penetration testing to comply with cardholder data protection requirements.
- Cyber Kill Chain: A methodology illustrating the progression of a cyberattack from initial recon to exploitation and beyond.
» Here's how to navigate the challenges of PCI DSS penetration testing
Tactics, Techniques, and Procedures (TTPs)
Red teams typically adopt adversarial moves that align with real-world hacking:
- Reconnaissance: Gathering network details, DNS records, and possible user accounts.
- Scanning: Using port scanners, network mappers, and vulnerability scanners.
- Gaining access: Exploiting weaknesses discovered, often aiming for admin privileges.
- Maintaining access: Planting backdoors or pivoting to other systems.
- Covering tracks: Hiding footprints to avoid detection.
Each phase reveals insights you can use to strengthen defenses. For instance, if attackers find it too easy to move laterally, you likely need stricter access controls.
Acting on Your Findings
Always investigate any reported weakness. Even “minor” findings can signal deeper systemic issues, so consider each result carefully. Adopt a continuous improvement mindset and review how your processes, technology, and staff training can adapt to block future threats.
» Learn more about penetration testing from pre-engagement to reporting
Common Challenges in Red Team Assessments
- Resource-intensive nature: Forming a highly skilled red team requires significant investment in talent, technology, and continuous training. These professionals need a blend of technical savvy and strategic thinking, making them expensive but invaluable.
- Collaboration and coordination: You must manage multiple specialists who excel in reconnaissance, social engineering, infrastructure exploitation, and more. Without robust teamwork, red team operations can stall.
Best Practices to Maximize Red Team Assessment Effectiveness
- First, secure leadership buy-in to ensure you have the budget and organizational support necessary for a thorough test.
- Second, clearly align testing objectives with your broader business priorities—this helps the red team focus on the highest-impact areas.
- Third, establish communication protocols across relevant departments so everyone knows their role once testing starts.
- Finally, prepare a follow-up action plan that outlines the steps, timelines, and accountability measures for addressing any discovered vulnerabilities.
Take Control of Your Security Testing Today
Red team testing is more than just a proactive measure—it’s a critical investment in your organization’s long-term resilience. By exposing your network’s blind spots using realistic adversarial tactics, you can stop cyber threats before they become catastrophic.
If you need trusted, expert-led red team testing, GRSee Consulting offers the depth of knowledge and proven methodologies to safeguard your environment. GRSee also offers flexible services like a virtual CISO to bolster leadership oversight and strategic planning.
From PCI DSS and ISO 27001 to SOC 2 compliance, GRSee’s holistic approach ensures you’ll stay ahead of ever-evolving threats.
» Proactively defend your business—contact GRSee today