Application Penetration Testing: Types & Essential Steps
Explore the importance of application security penetration testing and how it helps identify vulnerabilities in your applications, ensuring better protection against potential threats.
Published May 25, 2025.

When it comes to securing your applications, penetration testing is an essential practice to uncover hidden vulnerabilities. By thoroughly evaluating your system, this testing helps ensure that potential threats are identified before they can be exploited.
In this blog, we’ll explore the different application pentesting types and the key steps involved in conducting a successful test. Understanding these methods and processes can better equip you to protect your applications and reduce the risk of security breaches.
» Get expert penetration testing services tailored for both startups and enterprises
What Is Application Penetration Testing?
Application penetration testing is a systematic security assessment process that simulates real-world attacks to identify vulnerabilities in software applications and understand how they could be exploited.
The primary goals of a well-conducted application penetration test include:
- Identifying security weaknesses before malicious actors can exploit them.
- Demonstrating the actual impact of vulnerabilities through controlled exploitation.
- Evaluating the effectiveness of existing security controls.
- Providing actionable remediation recommendations that help organizations improve their security posture while meeting regulatory compliance requirements.
» Read more about the benefits and importance of penetration testing in cybersecurity
Application Penetration Testing vs. Vulnerability Scanning vs. Red Teaming
| Aspect | Application Penetration Testing | Vulnerability Scanning | Red Teaming |
|---|---|---|---|
| Approach | Attempts to exploit detected vulnerabilities | Identifies known vulnerabilities without exploiting them | Searches for a single entry point to advance laterally |
| Accuracy | Provides concrete proof of security flaws with fewer false positives | May produce false positives as no exploitation is attempted | Focuses on stealth, not comprehensive vulnerability discovery |
| Objective | Finds as many vulnerabilities as possible within a given scope | Recognizes vulnerabilities but does not assess real-world impact | Tests detection measures and lateral movement within systems |
| Security Team Awareness | Conducted with the security team’s knowledge | Typically automated and does not require security team involvement | Performed undetected to test if security teams can detect intrusions |
| Focus | Specific and remediation-biased | Broad vulnerability detection | Evaluates overall security posture and incident response effectiveness |
» Learn more: vulnerability scan vs penetration test
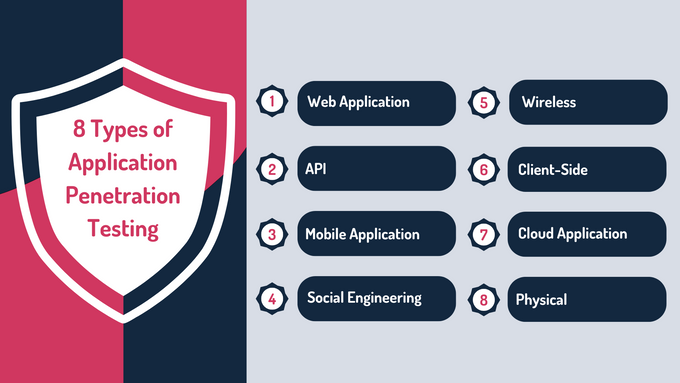
8 Types of Application Penetration Testing
1. Web Application Penetration Testing
This test assesses the web application's security by running simulated assaults to uncover vulnerabilities such as insecure design, coding problems, and database vulnerabilities.
Methodologies
- Pre-engagement: Defines scope, cost, and rules of engagement.
- Intelligence gathering: Collects information on the application using manual browsing, spidering, and brute-force techniques.
- Threat modelling: Assesses vulnerabilities and their potential impact. This evaluation allows the pentester to develop an action plan and methods of attack.
- Vulnerability analysis: Aims to actively discover vulnerabilities to determine how successful exploit strategies might be.
- Exploitation: Focuses solely on hacking vulnerable systems detected during the vulnerability analysis phase.
- Post-exploitation: Examines compromised systems for further access and sensitive data.
Challenges and Solutions in Web Application Penetration Testing
| Challenge | Solution |
|---|---|
| Lack of security awareness as third-party packages abstract developers from underlying technologies | Comprehensive training helps developers understand core security principles |
| Resource and time constraints delay security testing, increasing risks | Integrate security early in the SDLC |
| Automating customized attacks is challenging due to application-specific behaviors | Use automation to enhance attack efficiency |
» Learn more about secure development lifecycles
Real-World Security Incidents
Real-World Security Incidents
Sony PlayStation Network Attack (2011)
Hackers exploited an SQL injection vulnerability to breach the Sony PlayStation Network, exposing the sensitive data of millions of users.
Equifax Data Breach (2017)
A vulnerability in an Equifax application allowed attackers to execute SQL injection attacks, resulting in one of the largest data breaches in history.
» Understand how penetration testing can enhance your security
2. API Penetration Testing
APIs are crucial for integrating applications and services, making them a prime target for unauthorized access. API penetration testing focuses on identifying security vulnerabilities within APIs, which are increasingly targeted by hackers to access core data or functionality.
Methodologies
- Reconnaissance: Includes passive methods like gathering public data from sources such as GitHub and active methods like scanning for API directories.
- Vulnerability analysis: Uses fuzzing techniques to test API responses to unexpected inputs, focusing on JSON or XML structures.
- Exploitation: Attempts to leverage discovered flaws, such as bypassing authentication or exploiting weak input validation.
- Reporting: Summarizes vulnerabilities, assesses their business impact, and provides actionable remediation recommendations.
Challenges and Solutions in API Penetration Testing
| Challenge | Solution |
|---|---|
| API-specific vulnerabilities include authentication flaws, improper input validation, and business logic issues, leading to data breaches | Security professionals must undergo targeted training on API-specific threats and stay updated on emerging vulnerabilities |
| Scoping issues arise when clients limit testing, leaving gaps | Collaborate with clients to define a thorough scope, prioritizing critical assets |
| Misconceptions cause neglect in API protection | Promote awareness that all APIs need robust security measures, including secure coding, threat modeling, and regular penetration testing |
Real-World Security Incidents
US Treasury API Key Compromise (December 2024)
A compromised API key allowed unauthorized access to workstations and documents within the US Treasury Department.
Cox Communications API Breach (June 2024
Unauthenticated API endpoints enabled attackers to impersonate tech support, accessing and modifying customer data.
» Learn more: Why penetration testing is important for your business
3. Mobile Application Penetration Testing
Mobile applications handle sensitive user information. This testing assesses the security of mobile applications, focusing on vulnerabilities such as unprotected data storage, weak server-side controls, and inadequate transport layer protection.
Methodologies
- Pre-engagement: Defines the mobile pentest scope, including tested applications, testing methodologies (black, white, or gray box), and restrictions.
- Reconnaissance: Gathers information from the app’s manifest file, exposing permissions, API keys, and sensitive data.
- Vulnerability analysis: Identifies security flaws, focusing on insecure network traffic and API vulnerabilities.
- Exploitation: Attempts to bypass controls, access sensitive data, or compromise the device.
- Post-exploitation: Assesses compromised system value, examining stored sensitive data.
- Reporting: Documents findings for executives and technical teams, detailing vulnerabilities, impact, and remediation recommendations.
Challenges and Solutions in Mobile Application Penetration Testing
| Challenge | Solution |
|---|---|
| Rapid mobile technology changes introduce new attack vectors | Continuous learning and security research help professionals stay updated on emerging threats |
| Users frequently download unverified apps, increasing security risks | Security awareness training and risk evaluations mitigate threats |
| Limited resources delay security testing until late stages | Integrating security early in the development cycle helps detect vulnerabilities sooner |
Real-World Security Incidents
OyeTalk Android Voice Chat App Breach (2023)
A database misconfiguration exposed sensitive data, including IMEI numbers, and hardcoded secrets were revealed.
Chic-fil-A Mobile App Breach (2023
Credential stuffing attacks compromised over 71,000 customer accounts, leading to unauthorized transactions
4. Social Engineering Penetration Testing
Human error is a significant vulnerability in cybersecurity. Social engineering tests evaluate an organization's human-based attack surface by simulating phishing attacks to deceive employees into revealing sensitive information.
Methodologies
- Pre-engagement: Client approval is required, along with defining attack methods (e.g., phishing, impersonation) and setting restrictions.
- Reconnaissance: Information gathering includes naming conventions, address formats, and software use, with a focus on passive intelligence through social media.
- Vulnerability analysis: Identifies human weaknesses, such as phishing susceptibility and poor security protocols.
- Exploitation: Executes attacks like phishing, vishing, and impersonation to manipulate targets and access sensitive data.
- Post-exploitation: Assesses impact, including unauthorized access or malware planting.
- Reporting: Summarizes attack success rates and vulnerabilities, recommending security awareness training, policy enhancements, and technical safeguards.
» Did you know malware can bypass endpoint protection?
Challenges and Solutions in Social Engineering Penetration Testing
| Challenge | Solution |
|---|---|
| Social engineering tests can erode employee trust and morale if not handled sensitively | Provide immediate feedback and training to employees involved, emphasizing the educational aspect of the test to maintain morale |
| Social engineering tests can produce false positives or negatives, leading to misguided security strategies | Implement rigorous testing methodologies and validate results to minimize inaccuracies, ensuring that findings accurately reflect vulnerabilities |
Real-World Security Incidents
Colonial Pipeline Ransomware Attack (2021)
A phishing attack led to the compromise of an employee's credentials, allowing hackers to gain access to the network.
Ubiquiti Networks Breach (2021)
An employee fell victim to a phishing attack, leading to unauthorized access to sensitive data.
» Understand how to deal with ransomware
5. Wireless Penetration Testing
Wireless application penetration testing identifies security flaws in wireless networks that could lead to unauthorized access or data breaches, such as weak encryption, WPS vulnerabilities, and rogue access points.
» Read more: How to secure your wireless network with regular penetration testing
Methodologies
- Pre-engagement: Define scope, including authorized frequency bands, SSIDs, and testing restrictions after obtaining client approval.
- Reconnaissance: Identify wireless networks, SSIDs, encryption types, and signal strength.
- Vulnerability analysis: Assess weak encryption (WEP, WPA/WPA2), misconfigurations, and rogue access points.
- Exploitation: Attempt de-authentication attacks, brute-force WPS PINs, or crack WPA handshakes.
- Post-exploitation: Test lateral movement within the network after access.
- Reporting: Document vulnerabilities, attack success, and mitigation strategies.
» Learn more about encryption in our guide to asymmetric vs. symmetric encryption
Challenges and Solutions in Wireless Penetration Testing
| Challenge | Solution |
|---|---|
| Wireless networks may use MAC address filtering to allow only wireless cards with certain MAC addresses to connect | Use a tool like MAC Changer in Kali to spoof a MAC address and create an accepted value |
| Overly aggressive scanning or exploitation attempts can lead to denial-of-service conditions, impacting legitimate users | Carefully plan and scope the penetration test to minimize the risk of disruption |
Real-World Security Incidents
Tel Aviv Free Wi-Fi Network Hacking Incident
A resident discovered a buffer overflow vulnerability in the city's free Wi-Fi network, potentially allowing control over tens of thousands of users' traffic.
Orange Modems Leaking Wi-Fi Passwords
A vulnerability in Orange LiveBox modems exposed Wi-Fi passwords and SSIDs in plaintext, affecting nearly 20,000 modems.
» Understand how to fortify your business against password spraying attacks
6. Client-Side Penetration Testing
Client-side application penetration testing aims to uncover vulnerabilities in client software that attackers can exploit.
Methodologies
- Pre-engagement: Define the scope, specifying client-side applications, permitted testing techniques, and exploit limitations.
- Reconnaissance: Identify software versions, plugins, and user behaviors. Analyze client-side technologies like HTML, JavaScript, and extensions for vulnerabilities.
- Vulnerability analysis: Detect weaknesses in browser extensions, unvalidated redirects, and client-side controls. Review HTML and scripts for manipulative functionalities.
- Exploitation: Develop attacks targeting client-side flaws, such as malicious web pages or email attachments.
- Post-exploitation: Assess access gained and potential lateral movement within networks.
- Reporting: Document exploited vulnerabilities, methods used, and mitigation strategies, including patching and security best practices.
Challenges and Solutions in Client-Side Penetration Testing
| Challenge | Solution |
|---|---|
| Some bugs appear inconsistently, making them difficult to reproduce | Document steps, use debugging tools, and create repeatable test cases to ensure consistency |
| Client-side vulnerability testing can unintentionally crash applications | Obtain permission, throttle testing, and target specific areas to minimize disruption |
| Client-side vulnerabilities constantly change | Continuously learn from security advisories, real-world attacks, and fuzzing tools to stay updated |
Real-World Security Incidents
Fortnite XSS Vulnerability (2019)
An unsecured page had an XSS vulnerability, potentially allowing attackers to steal user data and virtual currency.
eBay XSS Vulnerability (2015-2016)
Attackers exploited an XSS vulnerability to gain full access to seller accounts, manipulate listings, and steal payment details.
7. Cloud Application Penetration Testing
Cloud application penetration testing aims to uncover vulnerabilities that could compromise the CIA of data and services hosted in the cloud.
Methodologies
- Pre-engagement: Define the test scope, including cloud services, applications, and infrastructure. Establish rules of engagement, agree on hostnames/URLs, and notify the owner of potential risks.
- Information gathering: Identify public information, map application content and network, and determine underlying technologies.
- Vulnerability analysis: Use scanners to detect weaknesses, validate findings, and assess password security policies.
- Exploitation: Actively hack identified vulnerabilities using tailored payloads.
- Post-exploitation: Evaluate compromised system value and maintain access.
- Reporting: Document findings with clear evidence for IT teams, management, and auditors.
» Did you know? The cloud might not be safe anymore
Challenges and Solutions in Cloud Application Penetration Testing
| Challenge | Solution |
|---|---|
| The dynamic nature of cloud services makes it difficult to assess vulnerabilities | Invest in training, use automated tools for mapping, and prioritize testing efforts |
| Cloud security requires expertise in web security, IAM, data storage, and networking | Pursue certifications, training, and hands-on experience through bug bounties or pro bono work |
Real-World Security Incidents
Capital One Data Breach (2019)
A former AWS employee exploited a misconfigured firewall to access sensitive data stored in AWS S3 buckets, affecting over 100 million customers
Pegasus Airlines Data Exposure (2022)
A misconfigured AWS S3 bucket exposed sensitive flight data due to employee negligence
» Discover how AWS penetration testing can help identify hidden risks
8. Physical Penetration Testing
Physical penetration testing seeks to uncover vulnerabilities that could allow unauthorized physical access to facilities and systems, potentially leading to data breaches or system compromise.
Methodologies
- Reconnaissance: Gather intelligence using maps, site visits, and discreet photography to assess security controls.
- Planning & preparation: Define scope, locations, and test phases. Establish a client contact and agree on a timeframe.
- Gaining access: Test security controls and personnel using techniques like social engineering.
- Exploitation: Locate sensitive data, find attack points, or remove assets without detection.
- Post-exploitation: Use gained access to uncover further vulnerabilities and critical information.
- Reporting: Provide detailed findings and remediation strategies for both executives and technical staff.
Challenges and Solutions in Physical Penetration Testing
| Challenge | Solution |
|---|---|
| Unauthorized testing can lead to legal violations | Obtain permissions, consult legal experts, and comply with laws and regulations |
| Repetitive testing patterns reduce effectiveness | Use varied methods to keep security teams alert |
Real-World Security Incidents
Google’s Physical Security Test (2005)
Google hired ethical hackers to test its security. Testers successfully entered restricted areas by tailgating employees and even accessed server rooms, proving that human vulnerabilities are a major threat.
Coca-Cola IP Theft (2009)
A former employee stole confidential formulas and attempted to sell them to Pepsi. Pepsi reported the attempt to authorities, but the breach emphasized the importance of restricting access to proprietary information and monitoring employee activities.
» Take your security a step further with pentesting and training in PCI DSS
How GRSee Consulting Stands Out in Application Penetration Testing
At GRSee Consulting, we begin application penetration testing by understanding your business goals and security concerns. We work with you to define the scope, reporting format, and systems to be tested. Our approach includes emulating real-world attacks to assess actual threats and risks.
What sets us apart is our comprehensive and hands-on approach to security testing:
- Beyond the basics: We go beyond automated scans, focusing on identifying high-impact vulnerabilities and uncovering business logic vulnerabilities that traditional tools and other vendors miss.
- Advanced hybrid testing: We combine strategic automation to quickly detect common vulnerabilities with manual deep-dive testing to uncover complex, hard-to-find security flaws that others miss.
- Tailored testing approach: Every test is customized to your unique environment, ensuring accurate and relevant results.
- Proven methodologies: We rely on battle-tested security testing standards, following OWASP’s full testing guide, OSCP methodologies, The Web Application Hacker’s Handbook, and SANS Top 25 to ensure a rigorous and effective assessment.
From scope definition to final reporting, we work closely with your team through kickoff calls, status updates, and post-assessment reviews. Our experts are available to answer questions, clarify findings, and help your team effectively implement security improvements.
» Contact us to start leveraging the benefits of application penetration testing