Asymmetric vs. Symmetric Encryption: How to Choose Between the Two
Choosing the right encryption method is vital for protecting data. Discover the strengths of symmetric and asymmetric encryption, and learn which is best for your security needs.
Published April 5, 2025.

Encryption is crucial for data protection in today's digital world, ensuring that sensitive information remains confidential and secure from unauthorized access. Without it, you risk exposing financial records, personal data, and proprietary business secrets.
Choosing the right encryption method is essential for a secure digital infrastructure, and symmetric and asymmetric encryption are the two most widely used methods, each with its strengths and weaknesses.
» Prepare for the future with robust encryption standards and SOC 2 certification
What Is Encryption?
Encryption transforms readable information (plain text) into a scrambled, unreadable format (ciphertext) using an algorithm. This ensures that intercepted data remains unintelligible without the decryption key.
It protects information in various contexts, including online transactions, secure communications, and cloud storage.
In modern cybersecurity, encryption is essential not only for securing communications but also for protecting sensitive data at rest (like files on servers) and in transit (information sent across networks). Properly implemented, it guards against data breaches, unauthorized access, and insider threats.
» Find out why the cloud might not be safe anymore
How Does Encryption Differ from Other Protection Methods?
Encryption stands out from other security methods in its ability to protect data even when it has been accessed by an unauthorized party.
This means that even if malicious actors bypass network security or insider threats steal data, they cannot decipher it without the necessary decryption key. This makes encryption essential in securing sensitive data against evolving cyber threats.
» Worried about your startup's security? Here are some cyber tips for your startup plan
Symmetric Encryption: How It Works
Symmetric encryption is the simplest and most traditional form, using a single shared key for both encryption and decryption.
This makes it faster and more efficient than asymmetric encryption, but securely sharing the key is a challenge. If an attacker intercepts the key, they can decrypt the data.
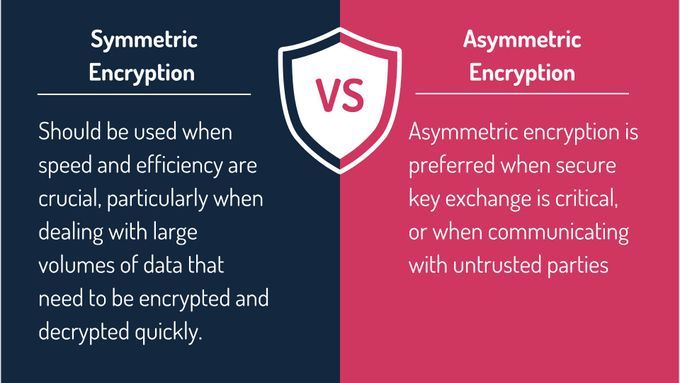
Despite this, symmetric encryption is widely used where speed and performance are crucial. It involves encrypting data with a secret key, transmitting it, and using the same key to decrypt it. It is typically used in environments where both parties have a secure method of sharing the key.
Common Symmetric Encryption Algorithms
1. AES (Advanced Encryption Standard)
AES is one of the most widely used encryption standards, adopted by governments, financial institutions, and tech companies alike. It supports 128-bit, 192-bit, and 256-bit key lengths, offering varying levels of security. AES is particularly valued for its efficiency and ability to protect both large and small data sets, making it a go-to choice for applications such as file encryption and disk encryption.
2. Triple DES (3DES)
Building upon the outdated DES algorithm, Triple DES applies the encryption process three times to enhance security. Though slower and less efficient than AES, 3DES remains in use in legacy systems, particularly in industries such as banking and finance.
» Did you know that attackers use encryption as well? Here's how to deal with ransomware
Real-World Applications of Symmetric Encryption
- Virtual private networks (VPNs): VPNs use symmetric encryption to secure the connection between your remote devices and corporate networks, ensuring that all data passing through the tunnel remains confidential and protected.
- File and disk encryption: Services like BitLocker on Windows devices use AES to encrypt entire hard drives, ensuring that your sensitive data remains secure even if a device is stolen or compromised.
- Secure messaging applications: Popular apps like WhatsApp and Signal employ symmetric encryption to secure your messages end-to-end, ensuring that only the intended recipient can decrypt and read them.
- Cloud storage solutions: Services such as Amazon S3 use symmetric encryption to protect stored data, preventing unauthorized access to files, even if someone gains access to your cloud storage account.
Symmetric Encryption: Strengths vs. Weaknesses
Strengths
- Faster encryption/decryption: Symmetric encryption processes data faster due to simpler operations, making it efficient for large volumes.
- Lower computational power: It uses less computational power than asymmetric encryption, ideal for limited-resource environments like mobile devices or IoT systems.
- Simpler key management: A single key is used for both encryption and decryption, simplifying key management in closed networks.
- Widely used: Symmetric encryption is standard in many applications, including file and disk encryption and secure communications like SSL/TLS for websites.
Weaknesses
- Key distribution problem: Securely sharing the encryption key is a major challenge—if intercepted, your data's security is compromised.
- Less secure for key exchange: Both sender and receiver need the same key, making secure transmission risky without extra protection.
- Limited use cases for open networks: Its reliance on secure key sharing limits use in public networks or with unknown users, making it impractical for the open internet.
Asymmetric Encryption: How It Works
Asymmetric encryption is more complex but offers a higher level of security than symmetric encryption for certain use cases.
This method uses two keys:
- A public key shared openly and can be used by anyone to encrypt your data
- A private key kept secret and is the only key that can decrypt the information
The beauty of asymmetric encryption is that it facilitates secure communication without the need to share the secret key, as in symmetric encryption.
The public key’s openness eliminates the need for secure key exchange. Only the private key holder can decrypt the data, ensuring security even if the public key is widely accessible. This makes asymmetric encryption valuable for secure communication between unfamiliar parties.
Common Asymmetric Encryption Algorithms
1. RSA (Rivest-Shamir-Adleman)
One of the oldest and most widely used public key algorithms, RSA is the standard for encrypting sensitive data transmitted over the internet. RSA is essential in the creation of secure websites (via SSL/TLS protocols) and is frequently used for email encryption and digital signatures.
2. Elliptic Curve Cryptography (ECC)
ECC is gaining popularity due to its ability to provide strong security with shorter key lengths. This makes it ideal for mobile devices and applications where your processing power is limited. It offers comparable security to RSA but with much faster processing times, making it more efficient in resource-constrained environments.
3. Digital Signature Algorithm (DSA)
DSA is primarily used for generating digital signatures rather than for direct encryption. It ensures the authenticity and integrity of your message by verifying the sender’s identity. DSA is commonly used in secure software distribution, digital certificates, and email encryption. Unlike RSA, which can be used for both encryption and signing, DSA is specialized for digital signatures and is often paired with other encryption methods to ensure both security and authenticity in communication.
Real-World Applications of Asymmetric Encryption
- Secure web browsing (HTTPS): When you visit a website secured with HTTPS, asymmetric encryption ensures that the connection between your browser and the website’s server is encrypted, preventing eavesdroppers from accessing your sensitive data like passwords and credit card information.
- Email encryption: Services such as PGP (pretty good privacy) and S/MIME use asymmetric encryption to encrypt your email communications. The public key encrypts the message, and only your private key can decrypt it, ensuring confidentiality even if the message is intercepted.
- Digital signatures: Asymmetric encryption enables digital signatures, which are used to verify the authenticity and integrity of your digital messages or documents. This is widely used in legal contracts, secure software distribution, and verifying your identity as a sender.
Asymmetric Encryption: Strengths vs. Weaknesses
Strengths
- Secure key distribution: With separate public and private keys, there's no need to share a private key over insecure channels, ensuring safe communication over untrusted networks.
- Better for authentication: It supports digital signatures to verify the sender's authenticity, ensuring data hasn't been tampered with and comes from a trusted source.
- Ideal for public networks: Since private keys don't need to be shared, it's well-suited for environments like the Internet, requiring secure, authenticated communication between strangers.
- Stronger security: The key pair enhances security for key management, making it ideal for scenarios demanding strong confidentiality, integrity, and authentication.
Weaknesses
- Slower performance: Asymmetric encryption is slower due to its complex algorithms, making it inefficient for large data or when speed is crucial.
- Complex key management: Managing two keys adds complexity in storing and securing the private key.
- High resource usage: Asymmetric encryption consumes more CPU and memory, posing challenges for systems with limited processing capabilities, like embedded devices.
Key Differences Between Symmetric and Asymmetric Encryption
| | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Key Usage | Uses a single shared key for both encryption and decryption, requiring secure key exchange. | Uses a pair of keys—public and private—eliminating the need for secure key sharing but adding complexity. |
| Speed and Performance | Faster due to simpler operations, suitable for large volumes of data. | Slower due to complex operations, ideal for smaller data sets and secure communications. |
| Key Distribution | The major challenge is securely distributing the key without malicious attackers accessing it. | Uses a public key for encryption and a private key for decryption, suitable for untrusted networks. |
| Security | Excels at encrypting large data volumes quickly once the key exchange is secure. | Provides stronger security for key distribution and authentication, ideal for secure communications over the Internet. |
When to Choose Symmetric vs. Asymmetric Encryption
Practical Use Cases for Symmetric Encryption
- Internal communications: Symmetric encryption is ideal for internal communications between departments or remote offices in a controlled environment where parties can securely share the encryption key.
- Large-scale data transfers: For transferring large files or sensitive data between databases or over internal networks, symmetric encryption provides the speed necessary without compromising security.
- Disk encryption: Encrypting entire hard drives, as done in solutions like BitLocker or FileVault, uses symmetric encryption to ensure that data at rest is protected without impacting system performance.
Practical Use Cases for Asymmetric Encryption
- Digital signatures: When authenticity is as important as security, such as in legal documents or digital contracts, asymmetric encryption ensures that the sender’s identity can be verified.
- Public key infrastructure (PKI): PKI systems, which are used to manage digital certificates and secure communications, rely on asymmetric encryption to facilitate trust between unknown entities over the Internet.
- Secure email communications: For email communications where confidentiality is crucial, asymmetric encryption (e.g., PGP) allows users to exchange encrypted messages without needing to securely share a secret key.
» Protect yourself from internet vulnerabilities by understanding phishing attacks
Understanding Hybrid Encryption
Hybrid encryption combines symmetric and asymmetric encryption. It uses symmetric encryption for fast, efficient data encryption and asymmetric encryption to securely exchange the symmetric key.
This method solves the key distribution issues of symmetric encryption while maintaining high performance.
Often used in protocols like HTTPS, hybrid encryption exchanges the symmetric key with asymmetric encryption before encrypting data with a symmetric algorithm. This balance of security and efficiency is ideal for applications requiring both speed and secure key exchange.
The Impact of Quantum Computing on Encryption
According to the University of Missouri, a quantum computer may be able to perform trillions of floating operations per second, potentially breaking traditional encryption methods like RSA and ECC by solving complex problems that classical computers cannot handle.
However, symmetric encryption, especially AES-256, could remain resilient to quantum attacks. It is nearly impregnable against brute force attacks, provided key transmission is secure.
As quantum computing evolves, post-quantum cryptography will develop new algorithms to maintain security against advanced computing capabilities.
How GRSee Can Help
GRSee Consulting offers expert guidance and solutions to help you navigate the complexities of encryption in today’s cybersecurity landscape. We can help you set up the key hierarchy, effectively providing you with a hierarchy that’s aligned with the standards. Encryption is secure and efficient, but its most important aspect lies in key management.
Moreover, we offer comprehensive encryption services to boost your security, including secure data transmission and best practices for protecting your sensitive information. As new technologies emerge, GRSee can also help you stay ahead by preparing your infrastructure for the future of encryption, ensuring that your data remains secure, regardless of evolving threats.
» Contact us to future-proof your security with advanced encryption standards